Why Traditional Cybersecurity Tools Cannot Defend Against Zero-Day and No Signature Attacks
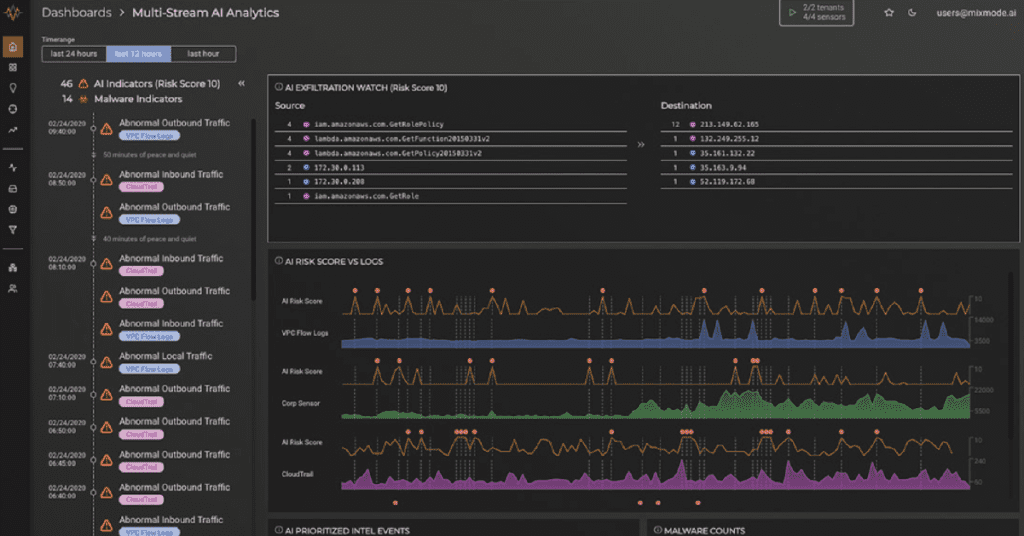
In our newest whitepaper, “Why Traditional Cybersecurity Tools Cannot Defend Against Zero-Day and No Signature Attacks,” we dive into how traditional cybersecurity tools work, why this fundamentally limits them from being able to detect zero-day or previously unknown attacks, why the industry standard for breach detection is around six to eight months and how modern, contextually-aware AI overcomes the limitations of traditional cybersecurity solutions.