Encryption = Privacy ≠ Security
For the past few years, many have been talking about the changing “threat landscape” as it pertains to the increase in zero day, insider and phishing threats. While all of these threats are on the rise, and constitute a concern, there is, perhaps, an even larger shift presenting a threat to enterprises – the shift to encrypted traffic.
Gartner estimates the upwards of 80% of all enterprise network traffic is now encrypted. While the proliferation of encryption has enabled a higher level of privacy for enterprises using the internet to communicate or transact business, many organizations are not suited to deal with the security implications of the increase in this traffic. Making matters worse is the fact that businesses are not the only ones to benefit from the increased availability of encryption. Malicious actors are using the same encryption technology to evade detection and conceal cyber threats.
Gartner states that 60% of all cyberattacks carried out in 2019 leveraged encryption; with that figure set to rise to 70% in 2020. With SSL increasingly becoming the standard enterprise protocol, cybercriminals are using encryption to conceal and launch attacks. This has become possible largely because SSL certificates are no longer difficult to obtain. Further complicating the issue is that, according to Sophos, less than 5% of organizations are decrypting their network traffic to properly inspect it. The result? The average enterprise is completely blind to as much as 50% of the malware on their network.
The Challenge of Encrypted Traffic
At the outset, it is important to understand that encryption protects the confidentiality and privacy of sensitive data on your network, however, it does not make your network secure from malicious actors. In fact, due to the aforementioned inability of most enterprises to assess their encrypted traffic, an argument can be made that for many enterprises the encryption of traffic actually poses a risk to their security posture. Simply put, if your security tools cannot inspect your network traffic payloads, they lose their ability to detect and alert you to threats.
Currently, many organizations do not have the ability to detect malicious content within encrypted traffic. Traditional script or intel-based network detections with bulk decryption, analysis, and re-encryption is not always possible (or secure) for performance and resource reasons. In the absence of these measures the only way for an enterprise to secure encrypted traffic is to be able to analyze and spot potential threats in the encrypted flows themselves.
MixMode’s Approach to Encrypted Traffic
MixMode supports the analysis of encrypted traffic, without the need for decryption, with our proprietary Third Wave Self-Supervised Artificial Intelligence. MixMode’s AI evaluates your network’s dynamic behavioral patterns and establishes a baseline for normal business operations. This baseline evolves with your network and provides the necessary context for the delivery of security alerts that are precise and actionable. More importantly, the MixMode solution provides results that are tailored to your specific deployment as opposed to solutions that are based on static training data.
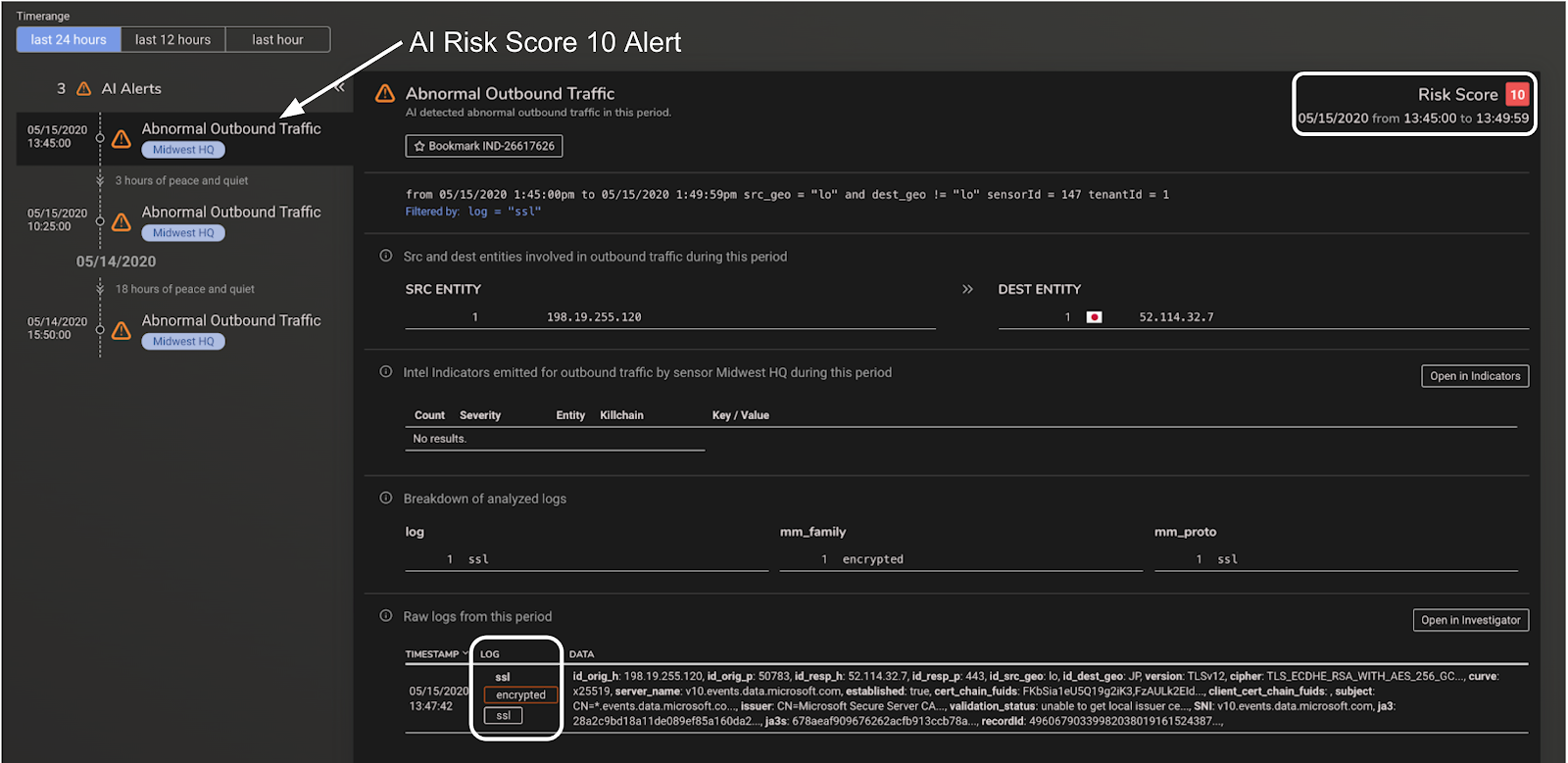
MixMode’s AI is able to leverage the header information available with encrypted traffic to look for patterns and anomalies that may indicate threats. Specifically, the AI analyzes various inputs around host-destination details and overall traffic behavior trends provided by network wire data, intel feeds and other private/public databases in real time. For example, when analyzing your network data, MixMode’a AI considers factors such as the day/time, host/source/destination information, the size of traffic between given IPs, frequency of traffic between IPs, etc. – most of which are still available to the platform with encrypted traffic! Using this information, MixMode is able to recognize and alert on anomalous encrypted traffic connections, that may indicate high risk activities, thereby raising awareness of potentially threatening activities and periods.
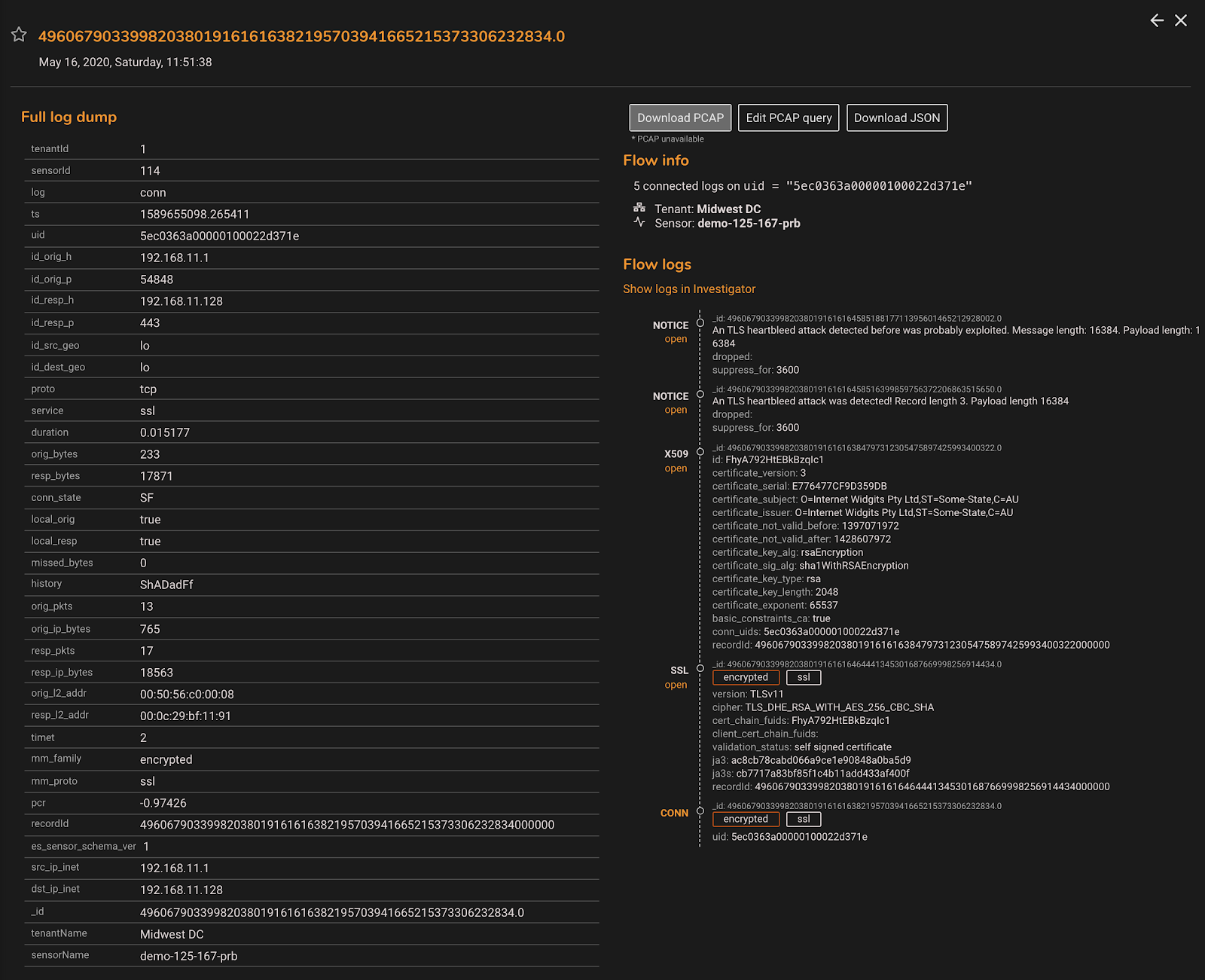
Once an anomalous encrypted flow is identified, an analyst can either use the forensic information available in the MixMode platform to assess the threat or decrypt just the specific traffic flows for further inspection. Either way, the enterprise has increased its security posture by analyzing this information.
The image below shows a MixMode AI Risk Score 10 Alert on an encrypted SSL Traffic Flow to an international geo.
The image below shows a sample of the forensic information available with in MixMode for an encrypted SSL Traffic Flow.
Interested in learning more on how MixMode’s self-supervised AI enables true anomaly detection without the extra noise allowing security teams to focus, see the entire attack surface, and catch attacks before damage is done? Contact our team today.


