Integrating MixMode with DeepInstinct
One of the biggest challenges facing enterprise security teams today is information overload created by massive tool sprawl. Many security teams are forced to utilize upwards of 40-50 security tools to monitor their environment which is leading to an overabundance of alerts. Recent reports showed that security analysts on average ignore up to 30% of security alerts completely which is leaving enterprises vulnerable to attack.
In many ways, MixMode was built as a platform to solve this issue by acting as a ‘single pane of glass,’ and allowing enterprises to combine multiple streams of security data like endpoint, firewall, Cloud and SIEM directly into the MixMode dashboard and providing advanced visualization and powerful AI filtering to ensure your data is actionable.
Recently we integrated MixMode with Deep Instinct, a powerful endpoint monitoring tool which allows security analysts to review DeepInstinct and MixMode data together on the MixMode dashboard. Bien Nguyen, Sales Engineer with Deep Instinct worked with the MixMode engineering team to make this integration possible.
“Deep Instinct is the next generation of endpoint security platforms. Considering that companies are changing so rapidly today, and their infrastructure with them, securing the endpoint on any OS, any place, at any time, has never been more critical.” Says Bien Nguyen of DeepInstinct
“Within the cyber security framework, integrations and strategic partnerships are crucial. There are no silver bullets and having best in breed solution integrations with other cyber security platforms is not a ‘nice-to-have’ anymore, it’s a business requirement for enterprises. Integrating with MixMode is a massive win not only for our two organizations, but the customers we both serve. MixMode’s comprehensive network traffic analytics platform is a crucial layer to our customers success securing their network and we are proud to be working with them and their team.”
We outlined the integration below:
Step 1 – Create a new sensor in the UI
Log into the MixMode platform UI
Navigate to the Sensors tab
Click on ‘Create sensor’ button
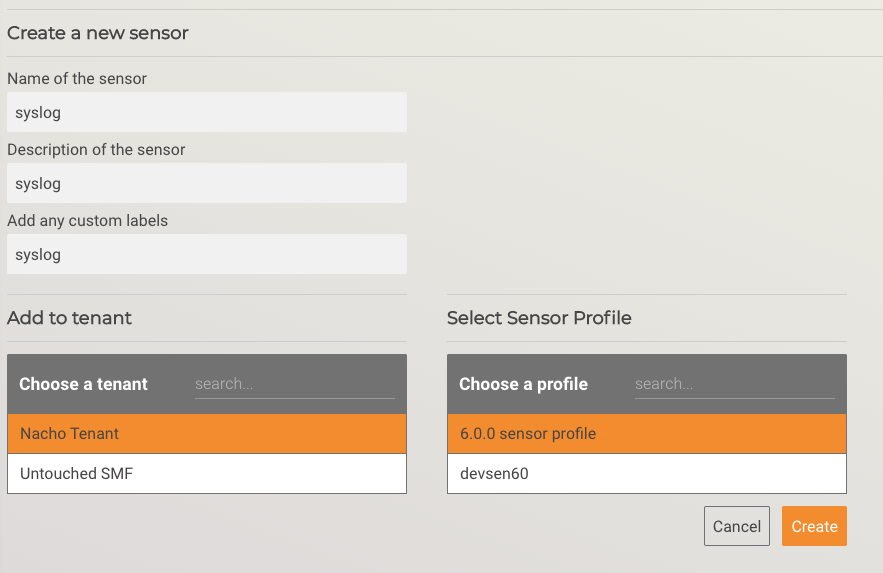
Fill in the required fields, and click ‘Create’
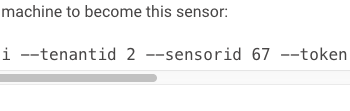
Open the new sensor information page to find the ‘tenantid’ and ‘sensorid’ values for the next step.
Step 2 – Receive and convert the syslog data
For our Proof of Concept, we created an AWS EC2 instance with a predefined port (10514) to receive the syslog data. Prior to integrating with DeepInstinct, a MixMode sensor was reconfigured to send syslog data it generates to this EC2 instance.
Per the following link: https://docs.aws.amazon.com/firehose/latest/dev/writing-with-agents.html, syslog data is formatted as follows:
SYSLOG — The RFC3164 Syslog format. Each log entry has the following pattern by default: “%{timestamp} %{hostname} %{program}[%{processid}]: %{message}”.
As described in https://www.rsyslog.com/doc/master/configuration/index.html, a configuration file was added to `/etc/rsyslog.d/` on the EC2 instance to accept the syslog data over port 10514 and convert it to a JSON object, adding MixMode required fields for upstream processing.
module(load=”imtcp” MaxSessions=”500″)
input(type=”imtcp” port=”10514″)
# output the straight message to a file
#action(type=”omfile” file=”/var/log/_prejson”)
# Load the json parser and re-format the message
module(load=”mmjsonparse”) #load mmjsonparse module for structured logs
template(name=”outfmt” type=”list” option.jsonf=”on”) {
constant(outname=”tenantId” value=”2″ format=”jsonf”)
constant(outname=”sensorId” value=”67″ format=”jsonf”)
constant(outname=”log” value=”syslog” format=”jsonf”)
property(outname=”ts” name=”timereported” dateFormat=”unixtimestamp” format=”jsonf”)
property(outname=”id_orig_h” name=”hostname” format=”jsonf”)
constant(outname=”id_orig_p” value=”10514″ format=”jsonf”)
property(outname=”id_resp_h” name=”hostname” format=”jsonf”)
constant(outname=”id_resp_p” value=”10514″ format=”jsonf”)
constant(outname=”id_src_geo” value=”lo” format=”jsonf”)
constant(outname=”id_dest_geo” value=”lo” format=”jsonf”)
constant(outname=”proto” value=”udp” format=”jsonf”)
constant(outname=”ps_family” value=”5″ format=”jsonf”)
constant(outname=”ps_proto” value=”50001″ format=”jsonf”)
constant(outname=”mm_family” value=”logging” format=”jsonf”)
constant(outname=”mm_proto” value=”syslog” format=”jsonf”)
property(outname=”message” name=”msg” format=”jsonf”)
property(outname=”facility” name=”syslogfacility” format=”jsonf”)
property(outname=”severity” name=”syslogseverity” caseConversion=”upper” format=”jsonf”)
property(outname=”syslog-tag” name=”syslogtag” format=”jsonf”)
property(outname=”source” name=”app-name” format=”jsonf”)
}
action(type=”mmjsonparse”)
action(type=”omfile” file=”/var/log/rlog/syslog_in.json” template=”outfmt”)
This formats each syslog data entry to match a syslog log entry from a MixMode sensor.
Check to make sure there are no errors in the config file by running: rsyslogd -N 2
Once the errors are corrected, run: systemctl restart rsyslog
Step 3 – Forward to the MixMode Platform
After the data has been converted to match the sensor syslog log entry, it needs to be transmitted into our platform. This is done using the same mechanism as the MixMode sensor: aws-kinesis-agent.
This requires:
- Installing the `aws-kinesis-agent`
- Configuring the credentials file (/etc/sysconfig/aws-kinesis-agent:
- # Set AWS credentials for accessing Amazon Kinesis Stream and Amazon Kinesis Firehose
- #
- AWS_ACCESS_KEY_ID=<secret key id>
- AWS_SECRET_ACCESS_KEY=<secret access key>
- AWS_REGION=us-west-2
- #
- # AGENT_ARGS=””
- # AGENT_LOG_LEVEL=”INFO”
- Configure the firehose agent (/etc/aws-kinesis/agent.json):
- {
- “cloudwatch.emitMetrics”: true,
- “cloudwatch.endpoint”: “monitoring.us-west-2.amazonaws.com”,
- “kinesis.endpoint”: “”,
- “firehose.endpoint”: “firehose.us-west-2.amazonaws.com”,
- “flows”: [
- {
- “filePattern”: “/var/log/rlog/syslog_in.json”,
- “deliveryStream”: “<firehose_path>”
- }
- ]
- }
- Starting the service:
- systemctl start aws-kinesis-agent
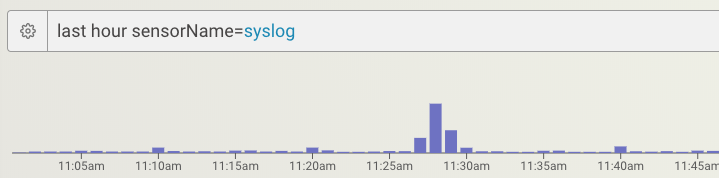
Step 4 – Confirm syslog data is present
In the MixMode user interface, open the Investigator page and search for data from that new ‘sensor’. I.e. `last hour sensorName=syslog`
The Goal: Make Security Data Actionable
The information overload problem that the industry is suffering from isn’t slowing down. In 2020 newer and more advanced threats are emerging posing major risks to enterprises while security teams are being hamstrung by subpar tooling and a lack of human resources.
MixMode is aiming to solve this problem by making security data from all of your platforms more actionable and allowing you to identify and remediate threats before they become catastrophes.


