Mixmode Blog
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Techiexpert: How Predictive AI Protects Against Ransomware, GANs and More
MixMode CTO and Chief Scientist, Igor Mezic, recently contributed an article for Techiexpert that examines three modern AI adversarial attacks, the financial toll they are having on some of our most important systems (including healthcare), and how predictive, third-wave AI is the only future-proof cybersecurity solution to protect organizations from these intelligent attacks.
Read MoreFeatured Use Case: Why a Large US Utility Company Turned to MixMode to Address Utility Grid Vulnerabilities
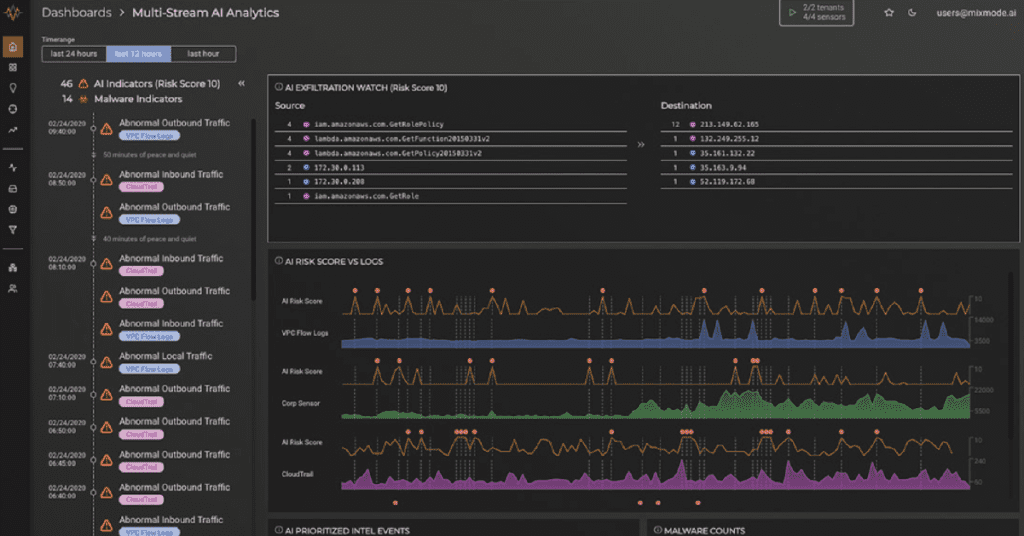
A large utility company approached MixMode with the following scenario: The enterprise SOC was utilizing a shared SIEM application that was being utilized by several stakeholders: the networking team, the SCADA team, the dev-ops team, the compliance team and cybersecurity teams for “basic search and investigation of log files to meet regulatory compliance requirements”.
Read MoreRecent Ransomware Attacks on U.S. Hospitals Highlight the Inefficiency of Rules-Based Cybersecurity Solutions
A number of recent high profile ransomware attacks on U.S. hospitals have demonstrated the urgency for organizations, municipalities, and critical services to take a proactive approach to protecting networks with a predictive AI solution.
Read MoreFeatured Use Case: Why a Large Government Entity Replaced Their SIEM with MixMode
Despite a three-year SIEM deployment and a two-year UBA deployment, government personnel needed an alternative to better detect and manage threats in real-time, as well as an improved platform for gathering comprehensive data.
Read MoreStop Patching Leaks in Your Cybersecurity Boat: A Streamlined Cybersecurity AI Solution to Adversarial Attacks
At MixMode our one algorithm is capable of catching any anomaly that may appear on the network. In contrast, other security programs rely on a reactive method of patching and constantly adding to their algorithms each time a hack occurs so that the network learns what to look out for.
Read MoreHow Vendors Capitalize on SIEM’s Fundamental Flaws
Because the fundamental nature of SIEM requires infinite amounts of data, security teams are forced to constantly wrangle their network data and faced with an unmanageable number of false positive alerts. This means they have to devise efficient ways to collect, organize and store data, resulting in an incredible investment in human and financial resources.
Read MoreThe Case Against Using a Frankenstein Cybersecurity Platform
The cybersecurity market has, simply put, been cobbled together. A tangled web of non-integrated systems and alerts from siloed systems. Enterprises are now being forced to utilize a “Frankenstein” of stitched together tools to create a platform that might cover their security bases.
Read MoreImproving on the Typical SIEM Model
Despite its inherent flaws, today’s SIEM software solutions still shine when it comes to searching and investigating log data. One effective, comprehensive approach to network security pairs the best parts of SIEM with modern, AI-driven predictive analysis tools. Alternatively, organizations can replace their outdated SIEM with a modern single platform self-learning AI solution.
Read MoreWebinar Recap: The Failed Promises of SIEM
MixMode teamed up with Ravenii to host a webinar focused on the history and evolution of SIEM platforms, their ideal role in a SOC today, and how they fall short as a threat detection tool in today’s modern cybersecurity environment.
Read More