Operational Technology Risk: Attack Paths, Challenges, and Protection for Vital Industrial Systems
I recently attended NTTSecurity’s webinar, “How to Shine a Light on Operational Technology Risk,” to learn more about current Operational Technology (OT) risks and the security challenges facing different industrial control systems (ICS) and supervisory control and data acquisition systems (SCADA). As a client success and support leader servicing customers in various OT sectors, I recommend this webinar for any organization seeking high-quality insights into OT impacts, challenges, as well as protection and response considerations for your vital systems.
Just as next-generation manufacturing lines have evolved to become a highly-intelligent brain of machine operations that far exceeds human capability, so have the intelligent, machine-led cyber attacks rendering enterprise networks inoperable today – threats that are virtually impossible for humans to contain or address in a timely manner.
What is Operational Technology?
To take a step back, OT is defined as the hardware and software that keeps power plants running, manages factory process lines, and works together to achieve an industrial objective such as manufacturing, transportation of matter, the generation of energy, etc.
In the context of network security, one of the biggest blind spots to a typical factory operation is the manufacturing line or factory floor. In many production lines there are smart tools to control devices that are frequently overlooked as threats to the network.
Who has access to the operations beyond the factory walls? Third-party vendors, contractors and vendors create risk. Which supplier is able to connect to your OT environment? What is transmitted? Is it secured?
Supply-chain attacks have dramatically changed the attack surface of the manufacturing network in the past few years, with more suppliers and service providers touching sensitive data via the (Industrial Internet of Things (IIoT) than ever before.
“More than 400 businesses were targeted every day in 2016, resulting in more than $3Billion in losses. 99% of all OT attacks are not detected,” NTTSecurity Webinar.
OT Attack Paths
Adversaries are always looking for new methods to attack networks with sensitive or proprietary data. For OT, NTTSecurity identifies potential attack paths as:
- Uncontrolled maintenance access to machines
- Unpatched control servers, PLCs, CPUs
- Non-hardened OS components
- Hardcoded usernames & passwords
- Web-based access without security
- Missing network segmentation, unknown data flow
- Unprotected gateways
Leading to the following possible impacts:
- Loss of production (denial of service)
- Manipulation of production processes
- Theft of Intellectual Property (IP)
- Lateral Movement
- Environmental influences
- Safety issues and/or destruction of machinery
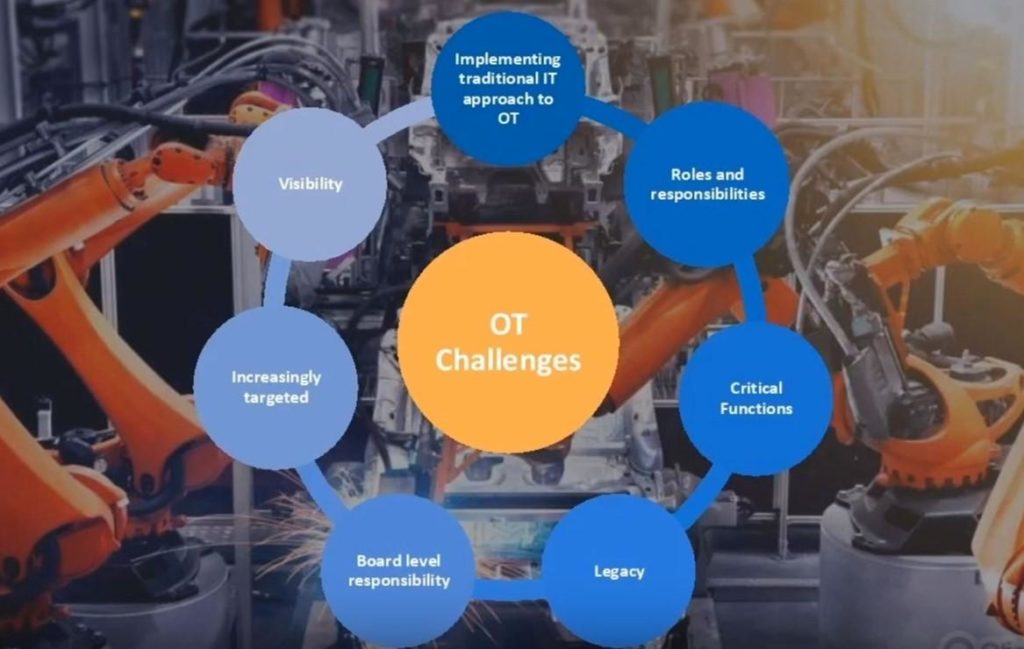
OT Challenges
NTTSecurity: How to Shine a Light on Operational Technology Risk
The evolution of OT systems includes IP based LAN and WAN networks, integrated enterprise systems, geospatial technologies, server virtualization, and mobile technologies. The sophistication and complexity of this environment has drastically increased the cyber threat profile for industrial enterprises.
The webinar listed 7 additional challenges facing OT:
1. Visibility: These systems have traditionally not been designed with monitoring, security, and visibility in mind. It can be difficult to detect and trend without this visibility, and have an understanding of what the network is doing / should be doing.
2. Targets are Increasing: Several high-profile attacks from a wide range of threatening actors (not just the rare nation-state attacks). It is clear these systems are now “in play” for general threatening actors.
3. Implementing a traditional approach to IT and OT will not work. For example, patching. In normal IT situations patching of security vulnerabilities can be made available quickly and regularly. For OT this is not the case. Patches are not produced or deployed as quickly and easily and it can be difficult to validate that they are successful.
4. Roles & Responsibilities: OT engineers & operators are not trained or traditionally focused on cybersecurity.
5. Critical Functions: There are real world impacts when there are issues with these systems. They need to be protected. Disruption to production lines equals loss of revenue as well as loss of reputation.
6. Legacy: Some of these OT systems are 30 – 40 years old. Applying security to these systems is a challenge particularly when the goal is zero impact on their production function.
7. Board Level Responsibility: Who owns the budget / responsibility for security for the OT environment? Is it the OT engineers, cybersecurity, networking?
How can you be positioned to protect and respond?
People, process, and technology. You must first have an informed, multi-disciplinary team. When it comes to process, you have to be open to changing and adapting how IT and network security work is done. Getting the right people and structure in place to empower the teams to make decisions is important. Lastly, for your tech stack, put the resources in place now to give the ability to monitor and have visibility into your OT networks.
You can watch the full NTTSecurity webinar on YouTube here.
By: Russell Gray, Director of Client Success


