The Alert Avalanche: Why Prioritizing Security Alerts is a Matter of Survival
One constant remains in the ever-evolving cybersecurity landscape: the barrage of security alerts. From firewalls to EDRs, security products diligently scan networks and systems, bombarding security teams with constant notifications of potential attacks. But what happens when the sheer volume of alerts becomes overwhelming? Enter the silent enemy—alert fatigue.
A Brief History of Security Tools and the Rise of False Positives
The genesis of cybersecurity tools can be traced back to the 1980s with the advent of the first antivirus programs. These were designed to detect and remove computer viruses, which, at the time, were relatively simple and easy to identify. As the internet grew, so did the complexity of threats, leading to the development of firewalls in the late 1980s to monitor and control incoming and outgoing network traffic based on predetermined security rules.
The Evolution of Threat Detection
The 1990s and early 2000s saw a surge in various cybersecurity threats, including worms, trojans, and spyware, opening security gaps. Security programs had to evolve rapidly, with new tools incorporating heuristic analysis and signature-based detection to combat these sophisticated threats. The introduction of intrusion detection systems (IDS) and intrusion prevention systems (IPS) marked a significant advancement in the ability to monitor networks for suspicious activity.
The Age of Machine Learning
With the explosion of data in the digital age, traditional security tools began to struggle with the sheer volume of threats. This led to the integration of machine learning algorithms in the 2010s, enabling systems to learn from data, identify patterns, and predict potential threats more accurately. However, this advancement was not without its drawbacks.
The Challenge of False Positives
As security tools became more sensitive and complex, the issue of false positives – benign activities mistakenly identified as threats – became more prevalent. False positives can be as damaging as missed threats, leading to wasted resources, disrupted operations, and desensitization to security alerts.
The rise of false positives has prompted a reevaluation of security strategies. Today, the focus is on fine-tuning detection mechanisms, balancing sensitivity with accuracy, and integrating human expertise with automated systems to discern critical risk from false alarms.
The Challenges of Security Teams: Drowning in Data, Starved for Time
Security teams are under immense pressure to identify and respond to real threats before they escalate into security incidents. However, the sheer volume of alerts creates a bottleneck. Analysts spend significant time sifting through false positives, leaving less time to investigate genuine threats.
Here’s how the alert deluge impacts security teams:
- Reduced Efficiency: Sorting through countless false positives impedes the investigation of true threats. This delays response times and increases the risk of successful attacks.
- Decision Fatigue: The constant barrage of alerts can lead to decision fatigue, where analysts become numb to the alerts’ urgency and make poor decisions. This can result in missed threats or inappropriate responses.
- Burnout and Turnover: The relentless pressure and long hours spent wading through alerts can lead to burnout and high turnover in security teams. This creates a vicious cycle – fewer analysts to handle the ever-growing number of alerts.
The Real-World Impact: Sleepless Nights and Breached Networks
The consequences of unaddressed alert fatigue extend beyond overworked security analysts. A stressed and under-resourced security function impacts an organization’s overall security posture.
- Missed Threats: Real threats can slip through the cracks when false positives consume analysts’ time. This allows attackers to gain a foothold in the network and launch attacks before they are detected.
- Delayed Response: Even when a genuine threat is identified, it may take longer to investigate and remediate due to the backlog of alerts. This extended window of opportunity gives attackers time to inflict significant damage.
- Security Silos: Alert fatigue can lead to security teams focusing on the tools generating the most alerts, neglecting other areas of security. This creates security silos, leaving vulnerabilities unaddressed.
From Alert Avalanche to Prioritized Action: Strategies for Success
So, how can security teams break free from the deluge of alerts and effectively prioritize threats? Here are some key strategies:
- Utilize Threat Intelligence: Integrating threat intelligence feeds with security tools helps focus alerts on known threats and threat actors. By aligning alerts with current attack trends, analysts can prioritize investigations.
- Invest in Advanced Analytics: Advanced security tools employing machine learning and behavioral analytics can differentiate between true threats and false positives, freeing analysts’ time to focus on critical alerts.
- Automation: Automating routine tasks like initial triage and response to low-risk incidents can significantly reduce security teams’ workload, allowing them to dedicate more time to complex threats.
- Incident Response Playbooks: Well-defined incident response (IR) playbooks help guide security teams through the investigation and response process. This streamlines their workflow and ensures a consistent approach to handling threats.
- Communication and Collaboration: Clear communication between security teams and other departments is crucial. Security teams must educate IT, developers, and other stakeholders about the importance of good security hygiene. This reduces the number of false positives caused by misconfigurations or accidental activities.
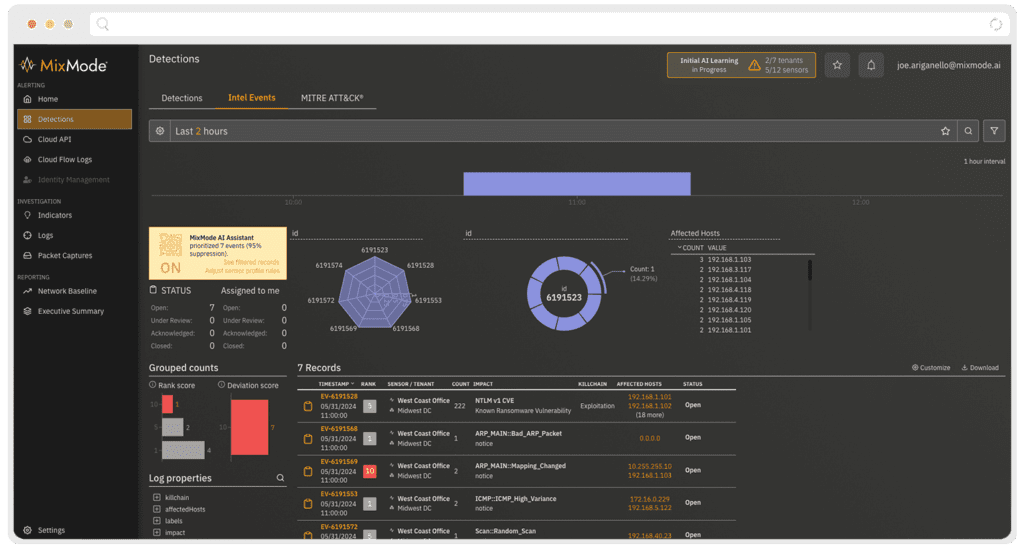
Streamlining Security Operations: MixMode’s AI-Driven Threat Prioritization
The MixMode Platform leverages Third-wave AI to ingest and analyze vast data sets in real-time. This automated threat detection process identifies and prioritizes only the most relevant security events, empowering security analysts to focus their expertise on the most critical issues, significantly streamlining security operations.
How MixMode Elevates Your Security Posture:
- Advanced Threat Prioritization: The MixMode Platform employs a multi-faceted AI scoring system to quantify each threat’s potential impact and likelihood. Analysts gain actionable insights to prioritize responses based on severity and relevance to their organization’s specific threat landscape.
- Enhanced Efficiency: The MixMode Platform automatically filters out false positives, allowing security teams to dedicate their time to high-priority threats. This significantly reduces response times and improves overall incident management efficiency.
- Data-Driven Decision Making: The MixMode Platform provides a clear view of your organization’s unique threat profile, allowing for proactive risk mitigation strategies. This data-driven approach fosters informed decision-making at all levels of your security team.
By leveraging MixMode’s AI-powered threat prioritization, security analysts can maximize their effectiveness and ensure a more resilient security posture.
In an upcoming blog post, we’ll dive deeper into how MixMode’s risk scoring works.
Looking Forward
The cybersecurity landscape is constantly evolving, and the tools at our disposal are becoming increasingly sophisticated. However, the human element remains central to effective security. By prioritizing security alerts, organizations can empower their security teams to focus on real threats and prevent security incidents. Remember, in the battle against cybercrime, prioritizing alerts is not just a matter of efficiency – it’s a matter of survival.
Take control of the alert cannon with MixMode.


.png)