As cyber threats grow more sophisticated, organizations are starting to turn to artificial intelligence (AI) to reinforce their security operations. But how widespread is the adoption of AI, and how effectively is it being leveraged?
MixMode set out to find out, partnering with the Ponemon Institute to survey cybersecurity professionals and find out where they stand with the adoption of artificial intelligence.
The result: MixMode is proud to release our inaugural report – The State of AI in Cybersecurity 2024 – offering valuable insights into the intersection of AI and cybersecurity.
The research examines the current cyber threat landscape and reveals that attacks are pervasive, with 45% of organizations experiencing phishing, web-based threats, or credential theft. This highlights the pressing need for advanced security tools, such as AI
Widespread and Sophisticated Attacks Highlight Need for Advanced Defenses
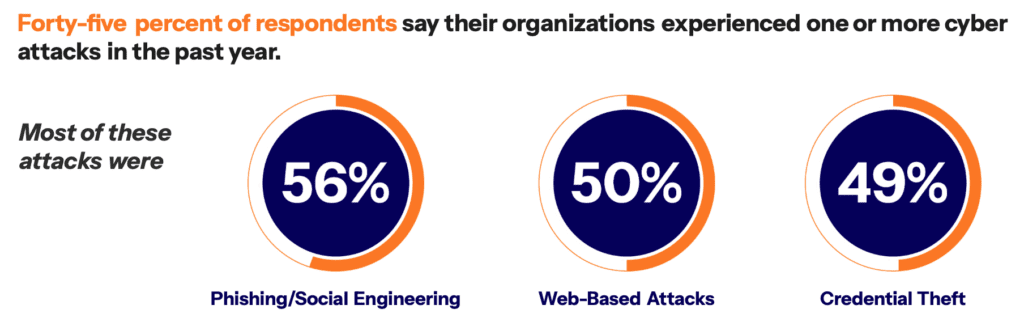
The report paints a stark picture of today’s cyber threat climate. 45% of respondents have had to contend with successful attacks over the past 12 months. Phishing attacks and social engineering attacks are prevalent, but web-app threats and stolen credentials are allowing access for ransomware, data exfiltration and other malicious activity.
The report findings highlight the diversity of paths attackers take to infiltrate systems. Legacy security systems are becoming more and more inadequate as they are blindsided by new attack vectors. AI solutions offer more adaptable detection for advanced attacks, based on patterns and anomalies rather than predefined rules. So as threat actors evolve, AI defenses can keep up with them to defend against potential threats.
Security Teams are Overwhelmed by Alerts, Yet Many Potential Threats are Still Missed
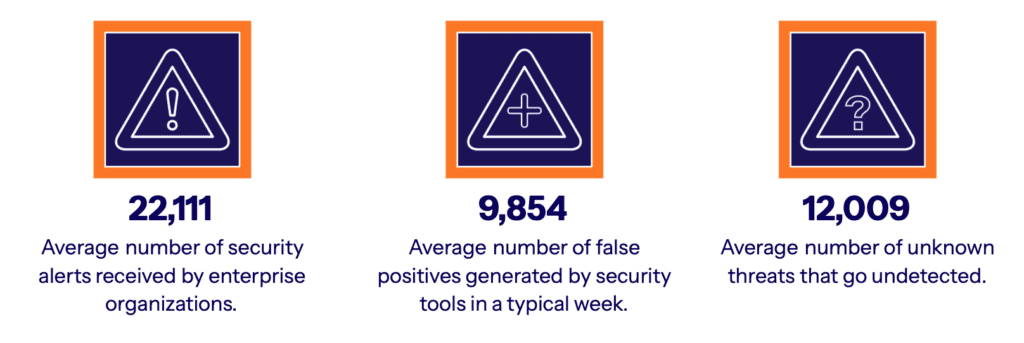
The findings also reveal that security teams face a bombardment of daily alerts. On average, respondents say they field over 22,000 alerts each week, relying on AI solutions to automatically review about half, while security professionals investigate 35%. Despite this deluge of alerts, costly breaches still wreak havoc.
Missed threats often sneak by due to the failings of rules-based systems or inability of machine learning to effectively review all alerts. False positives continue to overwhelm and desensitize security teams. Artificial intelligence with advanced capabilities would radically beef up security architectures, reduce false positives and catch advanced types of attacks that signal real threats. With an over reliance on machine learning techniques, more advanced AI adoption is still urgently required despite the moderate usage today.
The Integration of AI in Security Remains Gradual and Emerging
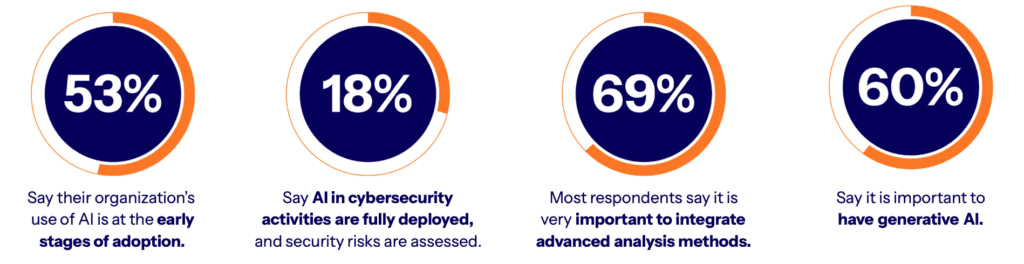
Most organizations are still tentative about AI security adoption. Over half of cybersecurity teams have only basic or intermediate AI controls in place for cyber defense. Just 18% claim full integration where AI defenses are deployed across an entire IT infrastructure, with risks continually evaluated.
This piecemeal adoption likely stems from the considerable growing pains organizations encounter when bringing AI online. Top challenges include simplifying complex legacy tech stacks before layering on AI, gaps in internal skills to implement and manage AI systems, and budget constraints. Addressing these barriers remains critical to smooth integration.
Targeted AI Sees Some Success Detecting Known Threat Patterns and Harvesting Threat Intelligence
Still, the findings confirm organizations actively utilize AI in significant ways. 65% leverage AI threat intelligence to rapidly uncover new suspicious activity or malware signatures. 67% run AI pattern recognition to detect attack behaviors that match known malicious tactics.
But with cyber attacks continuously evolving, over-reliance on matching attack patterns inevitably struggles with novel or unknown threats. AI solutions must continue advancing toward more autonomous analysis, hypothesis testing, and decision-making that surfaces relevant threats for analysts to apply human intelligence.
Realizing AI’s Full Potential Hinges on Holistic Implementation and Impact Assessment
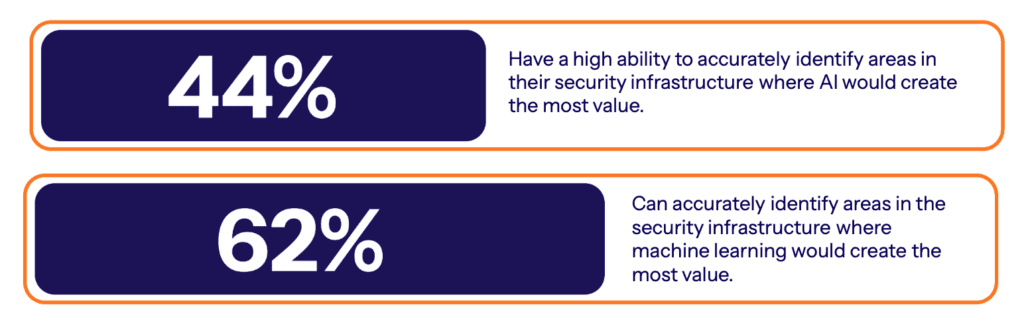
Even organizations using AI hit roadblocks expanding capabilities and measuring value, causing uncertainty around AI investments. Only 44% felt highly confident in identifying where AI can create maximum security impact within their tech infrastructure.
This likely relates to integration challenges like coordinating AI across on-prem, cloud, hybrid environments, and siloed tools – an issue for over 60% of adopters. Interoperability between AI implementations also needs addressing before broader rollouts. Tackling these obstacles will streamline scaling.
Mapping specific AI use cases to intrusion events and risk metrics will also help quantify impact and promote wider deployment. With threats proliferating, using AI to close operational and analytic gaps must remain a strategic priority.
The Pressing Need to Address Adoption Barriers As Attackers Accelerate Innovation

With threat innovation outpacing legacy security speeds, the need to capitalize on AI’s versatility is urgent. As adversaries harness AI themselves, fighting AI-driven cybersecurity threats with AI-based systems may soon become table stakes just to keep pace. By treating AI barriers as surmountable growing pains rather than roadblocks, organizations can pivot faster from incremental adoption to centralized, optimized AI protection against relentless modern attacks.
Click here to download the report today to learn more, and look out for our upcoming blog series where we’ll dive deeper into some of the report findings.
Other MixMode Articles You Might Like
MixMode Releases the First-Ever State of AI in Cybersecurity Report 2024
Harnessing the Power of Advanced AI to Optimize Security
Todd DeBell of MixMode Recognized as 2024 CRN® Channel Chief
Driving Towards Zero-Days: Hackers Take Turns Uncovering Exploits at Pwn20wn
Augmenting Legacy Controls with AI-driven Threat Detection and Response
Limitations of Legacy Cybersecurity Solutions Against AI-generated Attacks


