Webinar Recap: Why Your Legacy Cyber Platforms Can’t Defend Against Modern Day Attacks
Thank you to all who joined our recent webinar, Why Your Legacy Cyber Platforms Can’t Defend Against Modern Day Attacks.
In partnership with Ravenii, our 60-minute talk was hosted by MixMode’s Head of Sales and Alliances, Geoff Coulehan, CEO of Ravenii, Jeff Shipley, and MixMode’s CTO & Chief Scientist, Igor Mezic. They discussed key topics including:
- The new threat landscape of adversarial AI and intelligent bad actors
- Why rules-based security platforms are ineffective today
- How legacy platforms have completely failed to defend against modern day attacks
- How CISO’s and security teams are turning the tide with modern cybersecurity platforms that consolidate the tool stack and apply a next generation method of cyberdefense
To kick off the discussion, panelists discussed why rules-based security platforms are failing to protect and defend organizations in today’s threatscape.
The Aggregation Model is Falling Short
As we highlight in our recent whitepaper, traditional categories of NTA, SIEM, XDR and UEBA usually operate in the following way
- Aggregate historical information about network behavior.
- Normalize it for search and investigation.
- Write corresponding rules to trigger responses from the cybersecurity product.
- Run queries on a limited data set to detect anomalous behavior based on the aggregated historical behavioral insights.
At first glance, this may seem like a comprehensive approach, and in a bubble where only expected behavior occurs within limited data sets, it could be. In today’s threatscape, behavior and associated data is constantly changing and what’s acceptable one day could be anomalous the next (or vice versa).
Even if a dedicated team were to constantly input new rules, they could never fully capture the realities of a living, breathing modern network that might include hundreds or even thousands of connected BYOD devices, IoT sensors, server banks, cloud depositories…the list just keeps growing.
Creating rules on something that is going to happen is impossible and unattainable.
Coulehan mentioned that 15 years ago, breaches occurred when a bad actor made minor modifications to an already existing attack technique. Therefore to solve for this problem, rules-based and threshold-based detection systems were created to target these known signature attacks or a minor variance of them.
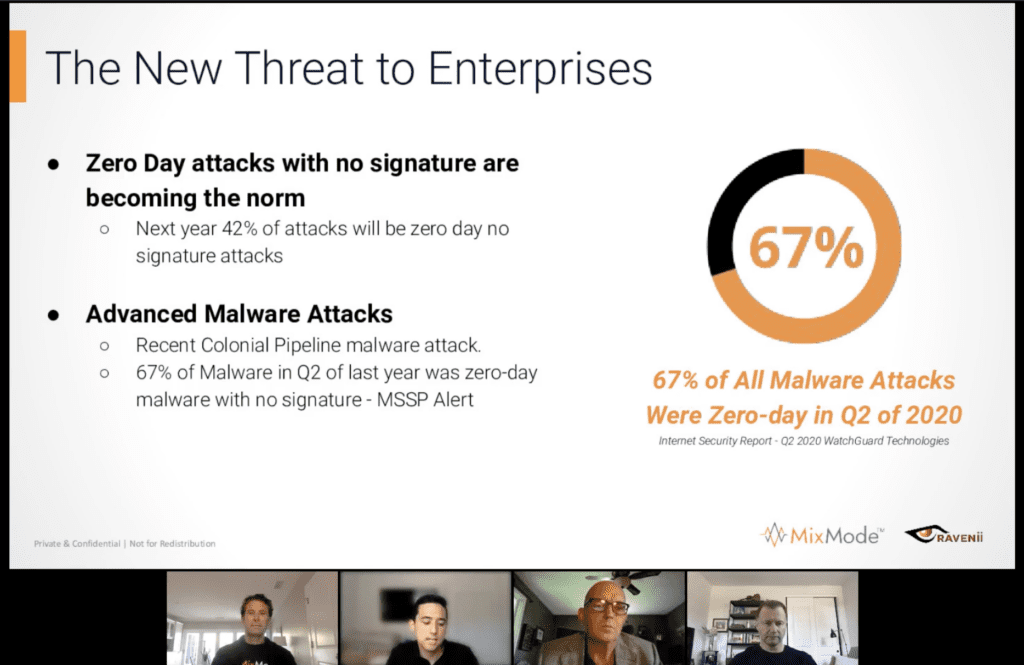
However, in 2021, what MixMode has seen across the board with our diverse customers – federal government, state agencies, and large enterprises – is an increase in advanced, coordinated attacks that don’t leverage known, existing techniques.
Furthermore, they aren’t as targeted as they once were. They are designed to infiltrate and exfiltrate as much information as possible with the intention of gathering it all, then applying other advanced analytics to exploit or manipulate behaviors at another time.
Rules have proven ineffective for these reasons and intelligent, adversarial AI is being built to side-step these rules-based platforms.
Cybersecurity Spend AND Attacks are Both Increasing Exponentially
Jeff Shipley continued the conversation into cyberspend and purchasing behavior saying, “There needs to be a change in the paradigm on how we detect and defend. The cyber attackers have access to the AI tools we have as well to create more sophisticated attacks. But people continue to buy point solutions that overlap on things that we already know.”
The enterprise threat landscape is changing fast. According to a recent study by Cybersecurity Ventures, over the last 10 years the number of successful cyber attacks has risen by over 500%. While this should be of major concern, even more alarming is the fact that spend on cybersecurity platforms has also risen alongside it.
Something isn’t working. More spend on cyber should mean better tools and more secure enterprises, right? But that just isn’t the case.
Today, the cost to operate a SOC has dramatically increased, thanks in large part to the additive nature of popular security solutions, each of which carries a hefty operational price tag to deploy, run, and keep these systems in tune.
Vendors tend to gloss over a glaring foundational issue related to stacking platforms on top of other platforms in order to achieve a singular goal: how to work within and across multiple siloes of proprietary data.
For some organizations, the result is a patchwork of incompatible, often redundant, tools. These “additive solutions” focus on essential security goals focused on system oversight. For example:
- Tapping into historical data efficiently.
- Aggregating and analyzing network events captured by endpoints and machine-generated data sources.
- Log collection
More Tools Does Not Equal Better Security
Jeff Shipley shared market feedback saying, “What we are seeing with a lot of customers is that having more tools is giving a false sense of security. You’re actually moving backwards as it relates to cybersecurity posture. You are just introducing additional access points for bad actors to hack into. You have put new software that could have holes that people can take advantage of.”
MixMode approaches this problem in a fundamentally different way. Using third-wave AI at the raw signal level, MixMode allows customers to store data in its raw, proprietary format without additional levels of normalization and extraction.
MixMode looks beyond data aggregation logs and applies third-wave AI intelligence to the raw signal, examining the indicators provided by that signal. The result is full coverage for the entirety of a network environment, free from the constraints and expenses involved with proprietary data movement and data retention.
With MixMode, organizations can truly invest in functional outcomes and the desired outcomes of the deployment of security platforms rather than needlessly creating expansive, siloed data lakes.
Get The Webinar On-Demand
This webinar is now available and available for on-demand download here.
The panel of experts also discussed:
- The recent Solarwinds Attack and their unsuccessful response
- Why and how log aggregation in cybersecurity is no longer effective
- What is Third-Wave AI and it builds a network baseline
- The benefits of cybersecurity platform consolidation – and why it’s important
Learn more about MixMode and how third-wave AI can help your organization overcome expensive data overload issues that are leaving your network vulnerable. Set up a demo today.


