MixMode and MITRE ATT&CK
Gain Insight into how The MixMode Platform integrates the MITRE ATT&CK Framework to detect and investigate.

Boosting Threat Detection with MITRE ATT&CK
MITRE ATT&CK is the gold standard cybersecurity knowledge base detailing the tactics, techniques and procedures (TTPs) used by adversaries across the attack lifecycle. It provides a common taxonomy for security teams to understand and combat threats.
The MixMode Platform fully integrates with The MITRE ATT&CK Framework, automatically mapping detections to techniques and tactics. This enables transparent ATT&CK coverage analysis and empowers users to validate visibility into threats mapped by MITRE.
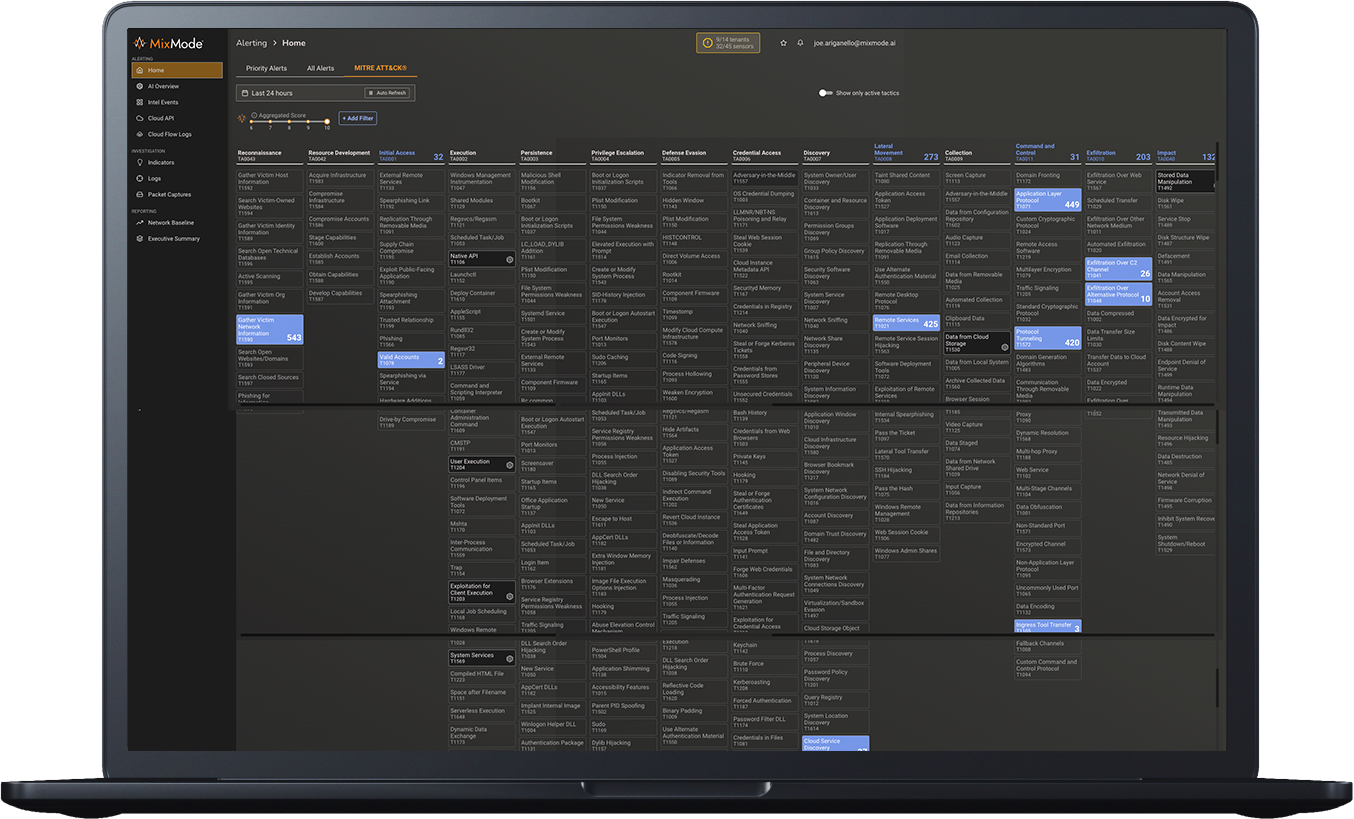
Real-time Threat Detection at Scale
The MixMode Platform provides customers unparalleled visibility into exposure to attacker TTPs catalogued by MITRE, highlighting threats moving laterally and progressing through the kill chain, as well as surfacing advanced techniques that evade other defenses.
MixMode uses MITRE ATT&CK in three key ways:
With MixMode's MITRE ATT&CK integration, security teams benefit from:
MixMode provides thorough coverage for the MITRE ATT&CK™ Framework Enterprise Matrix and has been proven to out perform competitive products in detecting MITRE ATT&CK™ TTPs. Coverage includes:
- Reconnaissance: The adversary is trying to gather information they can use to plan future operations.
- Resource Development: The adversary is trying to establish resources they can use to support operations.
- Initial Access: The adversary is trying to get into your network.
- Execution: The adversary is trying to run malicious code.
- Persistence: The adversary is trying to maintain their foothold.
- Privilege Escalation: The adversary is trying to gain higher-level permissions.
- Defense Evasion: The adversary is trying to avoid being detected.
- Credential Access: The adversary is trying to steal account names and passwords.
- Discovery: The adversary is trying to figure out your environment.
- Lateral Movement: The adversary is trying to move through your environment.
- Collection: The adversary is trying to gather data of interest to their goal.
- Command and Control: The adversary is trying to communicate with compromised systems to control them.
- Exfiltration: The adversary is trying to steal data.
- Impact: The adversary is trying to manipulate, interrupt, or destroy your systems and data.
Want to see a MixMode alert in action with MITRE ATT&CK?
Click the button on the right to walk through an investigation!

