For most enterprises, the detection of cyber threats and intrusions is primarily available in three locations: logs, endpoints and network data. Security teams collect event log information in a security information and event management (SIEM) for analysis and correlation. Endpoint tools provide a macro-level view of the communications between hosts. Network data provides an overall view into all connections and communications of all devices on your network.
Historically, network data was used as a forensic tool - a resource to research an event that was notified by one of these other platforms (SIEM, Endpoint or even Firewall). This is primarily because, at the time, network tools were not sophisticated enough to present alerts that were actionable.
The volume of data and simplicity of the rules engine and intel framework that powered these tools yielded an enormous number of false positives which made their proactive alerting functionality all but unusable.
With the proliferation of Artificial Intelligence in cybersecurity this has changed. This is exactly the type of big data problem that AI excels at. With the right tool, your network data can now provide you with most valuable, actionable alerts in your security stack. What follows is a discussion of some of the reasons why you may want to look to your network first when trying to identify potential threats or attacks.
Typical Security Stack
As mentioned above, the typical enterprise security stack includes a SIEM, endpoint protection and a firewall. In this section, I will discuss each, presenting some benefits and limitations to the security they can provide.
![]()
Security Information & Event Management (SIEM)
A security information and event management system is, “an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management system.” (TechTarget)
SEM performs collection, aggregation, and real-time monitoring of events and logs, while SIM correlates, normalizes, and then performs a later analysis and reporting on collected security records and logged data.
As a log aggregator, SIEMs were historically used for compliance purposes. They have grown in scope to be increasingly used for cybersecurity as well. Many companies position their SIEM at the center of their cybersecurity stack. This makes sense as these tools excel at aggregating data and providing correlations.
The issue with using a SIEM as your primary source of cybersecurity is that there are limitations to what logging can show and it requires constant tuning and refinement. Many companies feel as if they are perpetually deploying their SIEM. The dynamic network environments of today’s enterprise make it hard for security practitioners to feel confident that their logging is comprehensive and complete.
“Implementing SIEM continues to be fraught with difficulties, with failed and stalled deployments common.” Gartner
With the volume, variety, and speed of potential attacks on the rise, traditional SIEMs cannot keep up. The complexity of modern malware, data breaches, and security threats require a more proactive, agile approach to security infrastructure.
Endpoint Protection
Any corporate network that is being accessed from remote devices (laptops, phones, tablets etc.) needs endpoint protection. Endpoint protection has grown from the limited protection of antivirus software to a more comprehensive tool that includes next-gen antivirus, threat detection, investigation and response, device management and data leak protection.
Endpoint protection requires deployment to all devices accessing the network. This is complicated by companies employing BYOD policies and employees using personal computers over VPN. Endpoints also provide little protection for user-targeted attacks such as phishing, spear phishing or email-based malware payloads.
Moreover, by their very nature endpoint protection is reactive.
It is not uncommon for new malware signatures to take months before appearing in an endpoint system - making detections vulnerable to attackers. For these reasons, while valuable, an endpoint system should be viewed as only a piece of a comprehensive security program.
Firewall
The basic purpose of a firewall is to screen network traffic for the purpose of preventing unauthorized access between networks or hosts. A firewall is very good at blocking traffic. The risk is created in the exceptions and configurations that are required to make a firewall work in a given corporate network. As such, while it is a necessary security tool, a firewall does have limits and can lull an enterprise into a sense of false security.
Indeed, there are some pretty simple methods for attackers to bypass firewall protection.
For example, a typical firewall will compare all incoming data against a list of trusted/previously allowed programs to determine whether it should be allowed to pass. Hackers can easily get around this protection by creating fake data packets that look like they belong to trusted programs.
In addition, firewalls do not provide any protection against employees visiting websites with malicious code, using weak passwords or clicking on phishing emails. For these reasons enterprises should employ firewalls but use another tool - such as a network traffic analysis tool to verify that they are working as expected.
Importance of Network Data Traffic Analysis
While recent trends in cybersecurity have served to undermine the effectiveness of the aforementioned traditional tech stack, they have also highlighted the fact that network traffic analysis and attack detection technologies have emerged as the clear leader in the detection of malware and cyber threat activities.
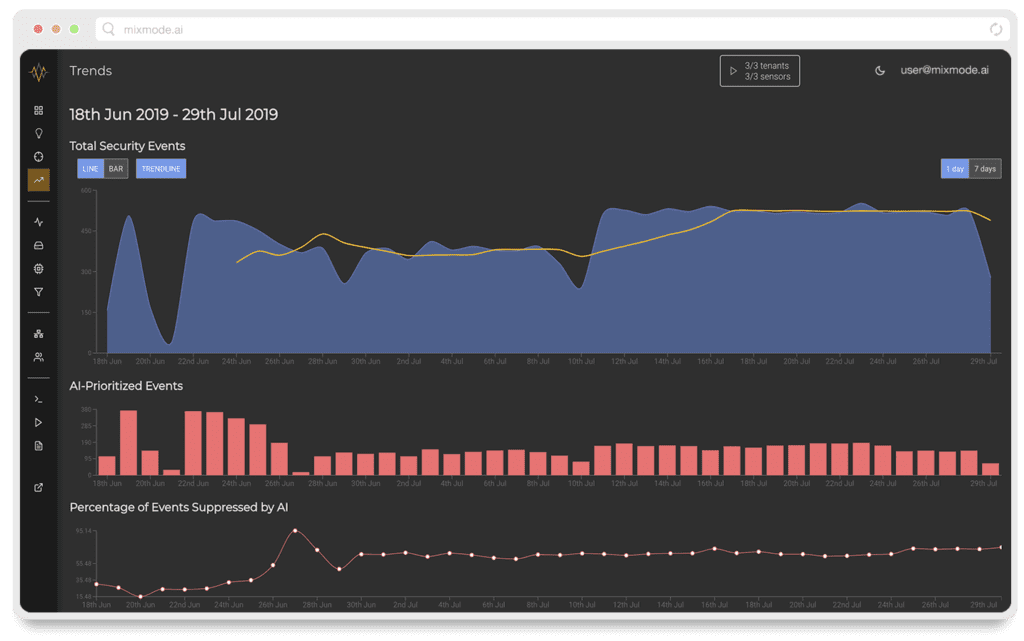
The key to this advancement has been the inclusion of artificial intelligence and its ability to ingest the large amounts of connection data, required for comprehensive coverage of a enterprise network, create a baseline of normal activity and detect usage patterns and anomalous behavior that may be indicative of potential threats.
By reviewing, recording, and analyzing the flow of information between two IP addresses, network traffic analysis tools, like MixMode, can provide the most accurate baseline of behavior within a network available.
Once created, this baseline can easily detect anomalies such as significant increases in bandwidth use, large outbound file transfers, regular micro-transfers to non-standard geo locations, distributed denial of service (DDoS) attacks, and other irregularities that may indicate that a company’s network security has been compromised.
Hackers can access a company’s network in several ways. As discussed above, many of the most common intrusion techniques target company employees (phishing, social engineering etc.). In many cases it only takes one infected device to compromise the entire corporate network. Generally speaking, this type of activity is not detectable via endpoint, firewall or SIEM.
Further, once inside your network, the malicious entity can disable endpoint protection, modify SIEM logs and logging and then use the compromised device to launch attacks against other users in the network.
While once considered exotic, today’s hackers routinely deploy malware that spreads throughout the network and function in a way that they are regarded as legitimate programs.
Network traffic analysis tools, like MixMode, monitors all activities on your network, not just at the perimeter, and are the ultimate source of truth for what is actually occurring between hosts and which endpoints are responsible for cyber attacks.
Why Network Data is the best starting point.
With this understanding of the importance of using network data for cyber security, the question is how can we make this data actionable and a valid starting point for identifying malicious activities.
Attackers can gain access to a company’s network, no matter how impenetrable it may seem. As such, taking preventive measures to defend your data is no longer sufficient.
The only way to minimize the damage and avoid huge profit loss is to detect cyber threats within the system, pinpoint where they’re coming from, and effectively terminate and stop the attacks. With cybersecurity moving from perimeter protection to speedy identification and remediation, there are 3 main deterrents to this:
- The volume and unstructured nature of the network data available to security teams makes it difficult to see what is happening and what actions should be taken.
- The lack of available resources (not enough people / time).
- Competing departmental interests (IT, networking, security, compliance, etc.)
Network traffic is the fastest way to detect an intrusion into your network and determine the scope of the potential breach. When you are under attack, there is a direct correlation between the time of infection and resolution, and lowering the cost of data breach for most companies.
Instead of solely focusing on tools and methods to prevent attackers from getting into their systems, today’s security professionals should invest more into how they can quickly detect, deter and remediate these attacks.
Network traffic analysis is the tool that is best situated to make extracting data more difficult for attackers. It can help you detect cyber threats more quickly and with a higher degree of certainty, thereby enabling you to remediate the threat more quickly.
How MixMode’s AI Makes Your Network Data Actionable
The power of MixMode’s Artificial Intelligence lies in the fact it is learning from the behavior of your specific network. As discussed above, the size and complexity of enterprise networks means it can be difficult to understand what is normal and what is a potential threat.
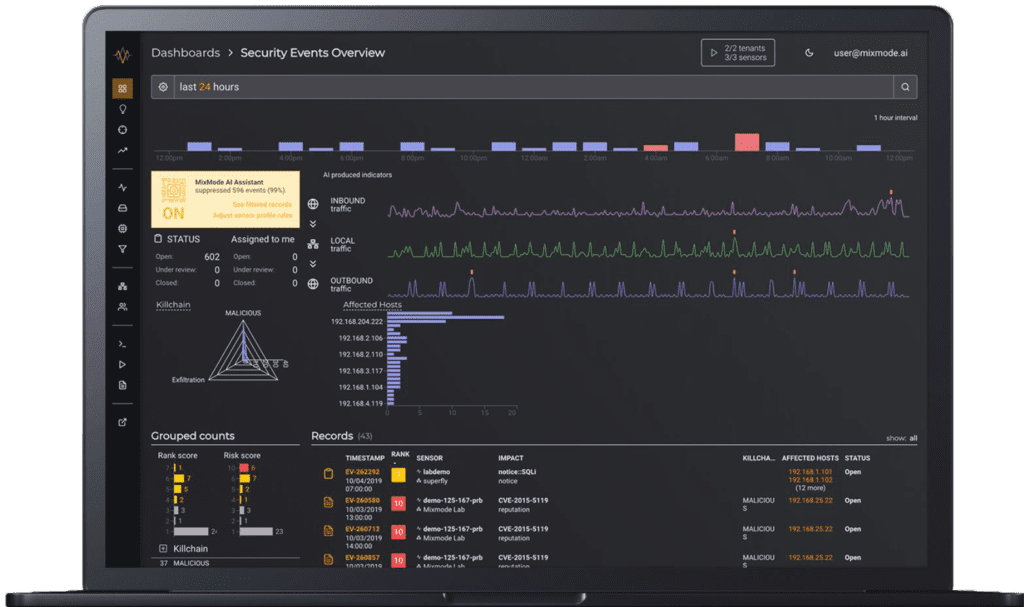
MixMode has solved this big data problem with its proprietary AI. Once a sensor is deployed, the AI engine analyzes various inputs around host source and destination details and overall traffic behavior trends provided by our forensic record, intel feeds and other private/public databases in real time.
When analyzing your wire data, MixMode considers factors such as the day/time, host/source/destination information, the size of traffic between given IPs, frequency of traffic between IPs, etc. to develop an understanding of what is the expected behavior for all of the IPs on your network.
This information is aggregated and processed through our proprietary AI engine and a predictive model of the "normal" behavior for your network is created. This is sometimes called a “generative model” as it is predicting the behavior of your network even if it has not seen similar behavior on it before. An initial baseline is produced in less than one hour, and this baseline is continually refined on an ongoing basis.
The end result is that MixMode AI delivers fewer alerts that are more actionable.
In fact, MixMode is able to consistently reduce the number of false positives, from intel-based alerts, by 90% or more versus historical systems.
Combining this reduction in intel-based alerts with proactive anomaly detection and alerting means your security team will have all the information it needs to detect malware, insider activities and zero-day exploits.
MixMode Articles You Might Like:
Using the MixMode query language to integrate with Splunk
3 Cyberthreats Facing Federal and State Governments in 2020
Staying CCPA Compliant with MixMode’s Unsupervised AI
5 Cybersecurity Threats That Will Dominate 2020
Wire Data: What is it Good For?
Yesterday’s SIEM Solutions Can’t Combat Today’s Cyberthreats


