Introduction
Detecting and defending against zero-day attacks is perhaps the biggest challenge facing the modern security practitioner.
Unlike traditional threats, zero-day exploits and attacks often fly under the radar, making prevention and detection especially difficult. In 2017, 25% of all reported breaches were caused by zero-day attacks. In 2018, that number rose to 37%.
Zero Day Attacks Are the #1 Threat Today
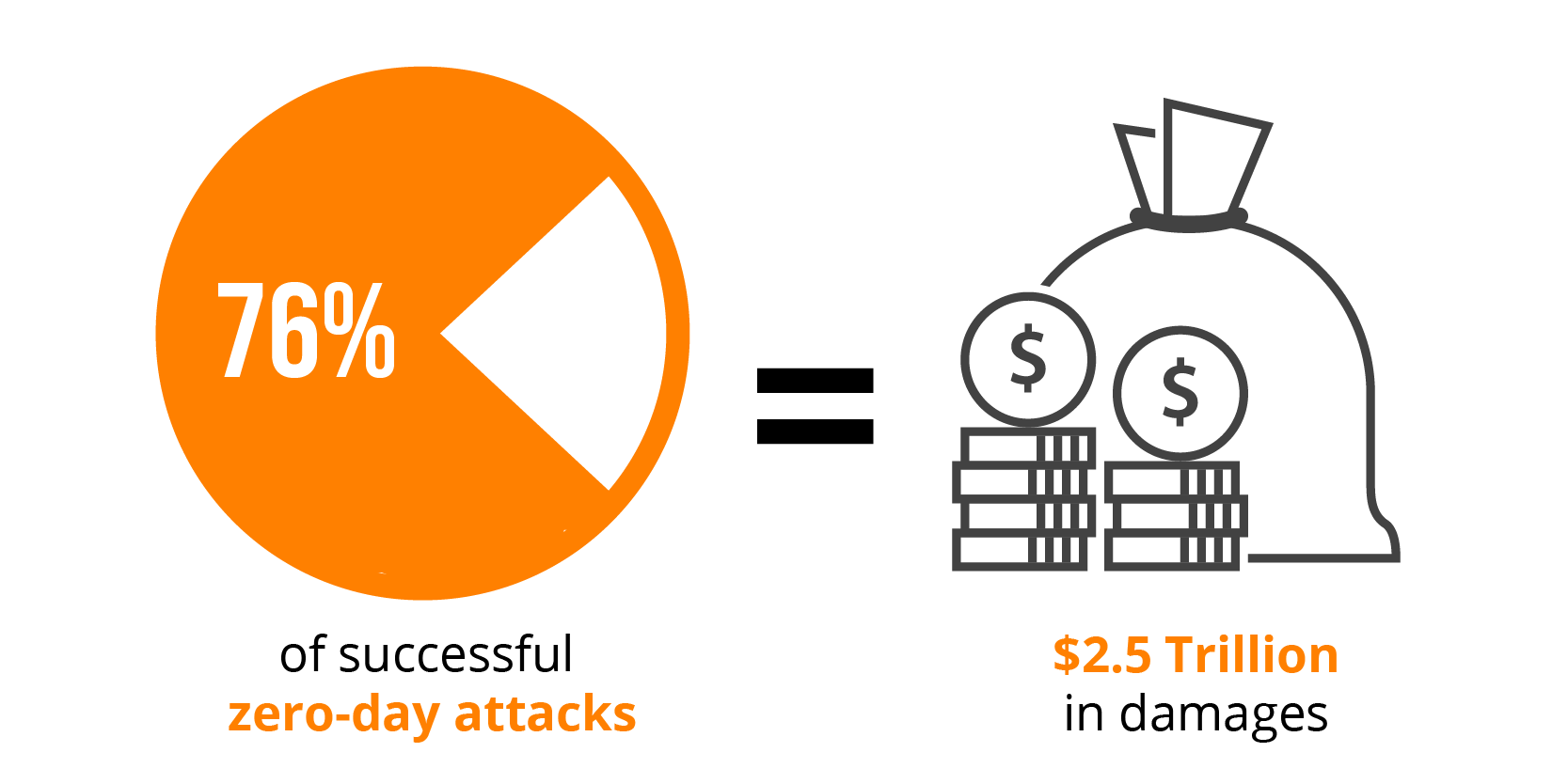
Ponemon Institute reports that a full 76% of successful attacks on organizations were zero-day attacks and expected to be responsible for damages of around $2.5 trillion in 2022 alone.
The reason for this is simple: the tools and techniques for developing and spreading zero-day attacks are becoming more readily available and more sophisticated.
This, unfortunately, has led to an increase in the complexity of detecting these attacks in a timely manner, before they do severe damage to an organization.
But this doesn’t mean prevention is impossible – with a comprehensive prevention strategy in place, organizations can greatly reduce their risk of being victimized by zero-day attacks.
In this post, we’ll discuss the basics of zero-day attacks, prevention strategies, and mitigation techniques to help security analysts, cybersecurity architects, and chief information security officers defend against these threats.
We’ll also explore the most effective methods for defending against zero-day exploits and attacks in 2023.
The 1-Sentence Strategy
Rather than detecting threats based on rules or an army of analysts, prevention is best achieved by monitoring baseline behavior to identify anomalous activity that could indicate a zero-day attack.
Why This Strategy Gives You A Sustained Advantage
By actively monitoring baseline behavior, security teams can be alerted when suspicious activity is detected, allowing them to quickly investigate and identify any potential zero-day exploit or attack before it has the chance to cause damage.
Operator theory, instead of rules, can be used to define what constitutes “normal” behavior and identify suspicious activity. This eliminates the need for manual effort and allows prevention efforts to scale with an ever-changing threat landscape.
This strategy can also be tailored to each organization’s unique environment, leading to more effective prevention capabilities and a sustained advantage against zero-day attacks.
Moreover, by continuously adapting prevention strategies over time, organizations can stay ahead of malicious actors who are constantly improving their techniques.
What Is A Zero Day Attack?
Generally, in cybersecurity, the term “zero-day” (sometimes referred to as 0 day) refers to the day when a new vulnerability is discovered in software and/or hardware.
For example, if a vulnerability is discovered on March 1st, it’s considered “day zero” (or 0-day). The term also refers to any attack that takes advantage of these newly discovered vulnerabilities before vendors can patch or fix them.
Vulnerabilities are flaws or weaknesses in software or applications that can be exploited to gain unauthorized access to a system.

In many cases, these vulnerabilities have not yet been discovered by security teams and/or the software developers, resulting in what’s known as a “zero-day attack.”
From that moment, of zero-day detection, the clock is ticking for a security team to produce a patch as quickly as possible.
Once a patch is produced, the software’s end users must install and verify the patch and security vendors must update their attack detection signatures and push those updates to their tools.
Unfortunately, it often takes a significant amount of time for these steps to be completed – during which the vulnerability remains unpatched and open, making it susceptible to attack.
A Quick History Of Zero Day Exploits
The first reported zero-day attack was on Microsoft Windows XP in 2004. Researchers discovered a flaw in the system that allowed attackers to gain access to and control a computer without any user interaction.
Then, in 2008, the first zero-day vulnerability was discovered in Apple’s Mac OS X operating system.
In 2012, a massive zero-day attack on Adobe Reader was uncovered and exploited to infect over 1 million computers. The impact of this attack was felt worldwide.
And in 2017, the large-scale WannaCry ransomware attack exploited a vulnerability in Microsoft Windows and caused an estimated $4 billion dollars in damages.
In 2015, the infamous Heartbleed bug posed a significant threat to web security as it opened up websites to zero-day attacks.
This is just a quick sample of the many zero-day attacks that have occurred in recent years – and it’s an indication of increasingly sophisticated techniques attackers are using to exploit vulnerabilities.
Many Attack Prevention Methods No Longer Work
As the threat landscape continues to evolve, prevention methods that were once considered effective are no longer reliable.
Firewalls and antivirus protection can effectively protect against known malicious files but they lack the ability to detect or prevent zero-day attacks.
Signature-based prevention systems may be capable of detecting previously unseen malicious files, but it can be difficult to keep these prevention systems up-to-date with the latest vulnerabilities.
Unfortunately, prevention is not always possible and organizations must rely on manual detection methods to mitigate zero day attacks.
The Problem With Manual Detection By A Team Of Analysts
When prevention systems fail, manual detection by a team of analysts is needed.
Unfortunately, manual analysis requires a significant amount of time and effort – often leading to costly delays in the detection process.
In addition, manually analyzing security logs can be tedious and time consuming. Analysts must sift through millions of events and data points to detect anomalies and malicious activities.
This means that even the most experienced security analysts can find it difficult to keep up with the pace of new threats.
And, at the end of the day, analysts are human.
They may overlook or miss important details which can result in the undetected exploitation of a vulnerability.
Zero Day Security Today In 2023
Since the early days of novel attacks, threats have become increasingly sophisticated and more difficult to detect.
Organizations must be more vigilant in their prevention strategies and mitigation techniques to ensure they are protected against zero-day attacks.
This means having the right systems, processes, and tools in place to detect suspicious activity from attackers attempting to exploit zero-day vulnerabilities.
How Modern Zero Day Attacks Work
Unlike the Microsoft attack in 2004 which was relatively simple, today’s zero-day attacks are often much more sophisticated and harder to detect.
Modern attackers often use a combination of techniques and strategies to bypass prevention measures.
Methods including memory corruption, code injection, social engineering, and manipulation of user credentials.
Additionally, attackers may use a mix of malicious payloads (e.g., ransomware, cryptominers) in an effort to evade detection and prevention systems.
In addition to prevention, organizations should also focus on threat intelligence gathering and analysis in order to identify and track suspicious threats.

Attackers Are Using Artificial Intelligence and Machine Learning
As attackers gain access to new technologies, from artificial intelligence (AI) and machine learning (ML) to automation tools and cloud computing platforms, the complexity of these threats continues to increase.
Today in 2023, zero-day threats remain one of the most difficult types of attacks for organizations to detect and prevent.
In order to effectively defend against these kinds of attacks, security teams must stay up-to-date with the latest prevention strategies and mitigation techniques.
Popular Vulnerabilities And Techniques Attackers Are Using Today
- Exploiting application programming interfaces (APIs),
- Taking advantage of unpatched software,
- Manipulating user credentials and authentication methods,
- Using remote code execution techniques,
- Deploying memory corruption techniques,
- Social engineering attacks (e.g., phishing emails or phone calls),
- Automation tools to launch massive numbers of attacks at once,
- Leveraging cloud computing platforms to launch distributed attacks.
- Using malicious payloads such as ransomware, cryptominers, and malware
- Manipulating Web Application Firewalls (WAF) and attacking the underlying infrastructure
- Exploiting insecure internet of things (IoT) devices to gain access to enterprise networks
- Leveraging public cloud environments for attack purposes
- Taking advantage of misconfigured systems or open source software vulnerabilities
- Abusing weak authentication methods like passwords
The tricky part is not only can these be hard to detect individually, but they often go undetected when used in combination.
Which means they don’t fit into traditional or rules-based security frameworks.
Security Teams Everywhere Are Struggling With False Positives
In addition to prevention strategies and mitigation techniques, security teams must also grapple with false positives.
False positives can often be caused by outdated or ineffectively configured systems, inaccurate signatures and rules, or incorrect detection of malicious activity.
While prevention methods such as application hardening and patch management can help reduce the number of zero-day threats, false positives can still be a major issue.
The simple reason is cost. As organizations strive to stay ahead of the latest threats, they often incur additional expenses for prevention and detection tools that generate false positives.

The resulting budgets can be difficult to manage – and with the growing complexity of zero-day threats, prevention tools are becoming more expensive.
For a large publicly traded organization like a Google or Facebook, this is simply the cost of doing business. These organizations can afford the computing power and prevention tools needed to remain secure.
But what about a regional bank? Or a municipal water supply? Or a healthcare provider?
These organizations are often at a disadvantage when it comes to prevention, detection, and defense against zero-day threats.
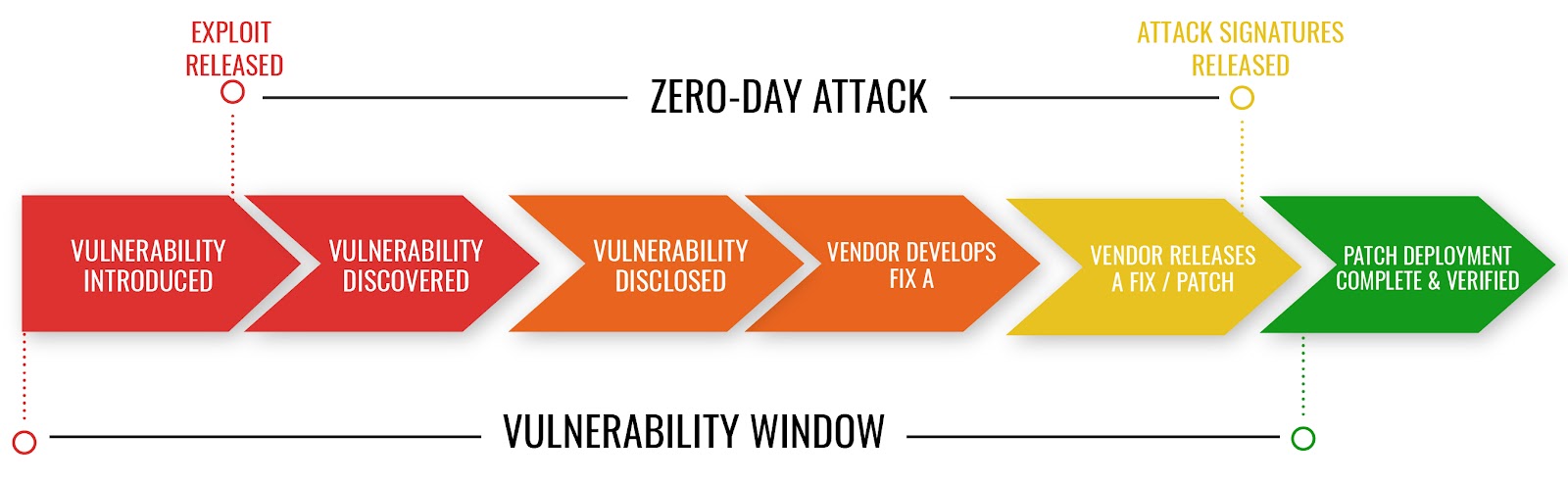
The 3 Phases Of A Zero-Day Event
Zero-day vulnerability
0 day vulnerabilities are the aforementioned flaw in a software code or in the way a piece of software interacts with other software that is yet to be discovered by the software vendor.
Zero-day exploit
A 0 day exploit based on a zero-day vulnerability; usually malicious software that uses a zero-day vulnerability to gain access to a target system.
Zero-day attack
The act of applying a 0 day exploit for malicious purposes;
“Zero-Day exploits, and their underlying vulnerabilities, have a 6.9 year life expectancy, on average”
Rand Corporation, “Zero Days, Thousands of Nights – The Life and Times of Zero-Day Vulnerabilities and Their Exploits.”
A true Zero Day attack occurs when perpetrators are using a vulnerability that is currently unknown to the software vendor, in order to compromise a system and perform malicious actions.
However, there also exists a form of “pseudo” zero-day attack where the exploit was already known to the software vendor but the cyberattack was still effective due to the failure of end-users to effectively update/patch their software.
This serves to highlight the inherent, ongoing risk of a zero-day vulnerability.
Zero Day Attack Prevention Is Challenging
While traditional security strategies like employing antivirus endpoint solutions, patch management and a sandbox certainly still have their place in cybersecurity, they are insufficient to detect and prevent zero-day exploits and attacks.
The simple reason for this is attack signature-based tools will not detect attacks that, by definition, have never occurred before.
Remember the 1-sentence strategy from before.
Prevention is best achieved by monitoring baseline behavior to identify anomalous activity that could indicate a zero-day attack.
With zero-day exploits, the source is often an unwitting internal user, and manifests in ways that are undetectable by traditional means.
Zero-day exploits are best identified by automatically recognizing aberrant behavior, and immediately alerting administrators to the change.
Therefore, to effectively deal with zero-day threats, organizations need to be more proactive and predictive with their security strategies.
Securing an organization means obtaining visibility and security for its entire data flow.
This requires visibility into traffic from every endpoint by dismantling each incoming file to search for any malicious elements whether they be known or unknown, while simultaneously looking at user and network behavior to be alerted to deviations and anomalies from expected activities.
The time when traditional security measures were effective has come and gone.
Best Practices For Mitigating Zero Day Exploits
The best prevention techniques for zero-day exploits are to:
- Regularly review and update software, operating systems and applications
- Create detailed policies on acceptable use of all technologies
- Educate employees about cyber security threats and their prevention
- Segment networks with firewalls
- Deploy advanced endpoint protection solutions that have the ability to detect unknown threats
- Monitor user activities and access levels
- Utilize multi-factor authentication
- Implement proactive security solutions that provide deep visibility into data flows and look for malicious behavior
This list can go on. But here’s the most overlooked best practice:
Be proactive.
Two-thirds of organizations take over 20 weeks to detect a threat. And another 20 weeks to remediate that threat.
Proactivity is key to prevention – it’s better to be prepared and prevention than reacting after the fact.
By having the right technologies, processes and people in place, organizations can be more agile when confronting zero-day threats by being able to detect them earlier and respond faster.
Artificial Intelligence & Zero Day Attack Prevention
As previously stated, zero-day exploits cannot be detected by conventional means, such as anti-malware or IDS/IPS devices because signatures have not yet been created.
This means that prevention must be accomplished by monitoring traffic and user activities, based on baseline behavior to detect abnormalities.

Origins Of AI And Zero Day Protection
Back in the early 2000s, the prevention of zero-day threats was focused on prevention through prevention of vulnerability.
This meant that the focus was on developing and deploying complex technologies such as firewalls or intrusion prevention systems (IPS).
The challenge with these solutions lay in their inability to detect vulnerabilities not yet known.
For this reason, prevention of a zero-day attack requires an understanding of the behavior of the user and system.
This is where Artificial Intelligence (AI) started to enter the picture – AI enabled systems could automatically recognize anomalies within normal user activity, or detect new malicious software based on its behavioral characteristics.
Strengths Of AI-Based Threat Detection
AI-driven solutions are better equipped to deal with the dynamic nature of zero-day threats because they can detect patterns in data that humans cannot see.
In addition, AI solutions have fewer false positives than traditional prevention strategies, thereby reducing the risk of a false alarm.
Without specific detection capabilities, security administrators have to rely on behavior-based detection methods.
Behavior-based detection: techniques look for characteristics of malware based on the way it interacts with the target system.
This means a solution using a behavior-based technique doesn’t examine the code of incoming files and traffic flows, but instead looks at the interactions they have with existing software and tries to predict whether this is the result of any malicious action.
Machine learning is often used to establish baseline behavior based on data of past and current interactions within the system.
As with statistics-based detection techniques, the more data that is available, the more reliable the detection becomes.
A behavior-based detection system that works on a single target system for a long time may prove very effective in predicting results of current processes and actually detecting malicious software.
The Failed Promises Of AI-Based Threat Detection
Despite the promise of prevention through AI-based solutions, there are still a number of challenges that need to be addressed.
First and foremost is the issue of scalability.
AI-driven solutions need to be able to detect threats across an entire network, but this requires them to collect data from all points in the system.
AI Has Historically Struggled To Detect Fast Enough
For all their strengths, Deep Learning and other neural networks have encountered a major stumbling block – speed.
Traditional prevention solutions can be deployed quickly and widely as soon as they are recognized, but AI systems need to ‘learn’ before they can detect new threats.
This means that the time between an attack emerging and being detected is longer than it would with traditional prevention techniques.
This is why AI-driven prevention has been met with criticism and skepticism – many organizations feel that it is not fast enough and may be ineffective against certain types of attacks.
Enter Third-Wave, Context-Aware AI
The core approach of modern AI is supervised learning, which involves using data that represents the phenomenon of interest in order to train machine learning models built on artificial neural networks.
The threat of Zero Day attacks, for which no effective anti-malware solution exists hangs over supervised machine learning based cybersecurity solutions, just as it does over older signature-based cybersecurity defenses.
Second-wave AI is not proficient at detecting attacks because it is not good at detecting that which it has not been trained to see.
Having a machine learning model that has learned only one rigid behavioral attack vector makes a cybersecurity program vulnerable to dynamically changing attack signatures.
If the ML-learned normal attack vector is too broad, it’s at risk of blocking an excessive number of legitimate behaviors as cybersecurity attacks.
If that pattern is too narrow, the cybersecurity program is at risk of permitting a wide range of actual attacks to proceed unchecked.
You cannot train an ML model to detect a threat for which there are no extant examples in the historical record.
Third-Wave AI is a new approach to addressing Zero Day threats
“Today’s AI relies on an unsupervised learning methodology capable of understanding its environment based on its own, changing context. This is different from anything else currently available on the market.”
Dr. Igor Mezic, MixMode CTO & Chief Scientist
By leveraging context-aware data, Third-Wave AI can provide a more comprehensive cybersecurity prevention strategy.
Context-aware data is created by leveraging the relationships between objects and their environment to detect anomalous behaviors, rather than simply relying on pre-defined attack vectors or signatures.
Context-aware AI takes into account the behavior of an attack across multiple devices, platforms and networks in order to more accurately detect malicious activity.
It relies on an unsupervised learning methodology capable of understanding that the environment is changing based on the contextual information it observes.
Specifically, it observes the totality of the information available to it from the network sensor and detects any unusual behavior, be it on the lateral movement, inbound traffic or outbound traffic.
A Real Application Of Third Wave AI And Zero Day Attack Protection
The City of Phoenix came to MixMode with a number of potential needs in their Security Operations Center. One gap they had in the cities security posture was that they had no means of detecting “novel”, or never before seen attacks. The tools in place at the City had no ability to detect cyberthreats that were not in a threat intel feed or detectable by a rule they had written. This was leaving the City vulnerable.
MixMode worked with the City’s cybersecurity team to deploy a next-generation SOC platform using Third Wave Artificial Intelligence to enable real- time visibility into all threats and anomalies in their network, both known and novel (like zero-days), consolidate their legacy toolset, and improve the productivity of their SOC team. Within the first 24 hours of deployment, absent any human operator involvement, MixMode provided this visibility into and context for active, real- time attacks as well as network and configuration inadequacies that had gone undetected by all their other cybersecurity tools and their human operators.
The visibility that MixMode provided in those first 24hrs resulted in the City taking immediate action to resolve the issues and ultimately strengthen its defenses. By eliminating unnecessary SIEM and UEBA costs, The City was able to fully fund the MixMode deployment, gaining real-time and novel threat detection, without losing the functionality they got from their SIEM and UEBA deployments.
A Simple Example
For example, a Third-Wave AI system might detect that a particular user is accessing resources from an unusual location.
The AI would then observe the behavior of the user and determine whether or not it fits into the normal patterns for that user.
If it does not, then further investigation can be done to assess whether or not the behavior is malicious.
In this way, AI-driven prevention systems can identify threats that traditional prevention techniques may have missed.
This method of prevention is particularly well suited to rapidly evolving attack signatures and zero day exploits, making it an essential tool in any modern cybersecurity prevention strategy.
How You Can Learn More About Third Wave AI
The best way to learn more about Third-Wave AI is to read up on the latest advancements in supervised and unsupervised machine learning.
You can also speak with cybersecurity experts who specialize in this technology, or join a dedicated professional network to stay up-to-date on the latest developments in prevention strategies.
Helpful Resources
Defenses Against Zero Day Attacks In 2023
Zero Day attacks can be a dangerous and costly threat to any organization’s security.
However, with the right prevention strategies in place, such as those powered by Third-Wave AI, organizations can have peace of mind knowing they are protected against these kinds of threats.
Organizations should invest in prevention strategies that focus on context-aware AI, which are better suited for detecting zero day exploits.
As its own behavior is adaptable to new network conditions, it makes it almost impossible to fool by hackers, even those using modern machine learning penetration methods.
This enables constant adaptation to evolving security conditions and robust zero-day detection of security events that have never been observed before ushering in a new era in cybersecurity.
It is also important to have prevention strategies in place that focus on prevention from the network level and beyond, such as user authentication and encryption methods.
Finally, organizations should consider investing in specialized threat intelligence systems which are designed to detect and alert security teams when new and unknown threats emerge.
By investing in prevention strategies powered by Third-Wave AI, organizations can stay ahead of the most sophisticated zero day attacks in 2023.
And it is only with this kind of prevention that they will be able to protect their reputations, company interests and avoid costly breaches.
Other MixMode Articles You Might Like
How ChatGPT Will Help Hack Your Network
Getting Ahead of the Adversary with Third Wave AI
2022 Cybersecurity Statistics You Should Know About
New CISA Strategy Focused on Resilience, Inevitability of Data Breaches
Video: Modernizing Phoenix’s Cybersecurity to Combat Nation-State Attacks
Financial Services IT Teams Relying on Legacy Cybersecurity Plagued By False Positives and Negatives


