Mixmode Blog
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The Top 8 Concerns for CISO’s in 2020
Although a relatively new corporate position, Chief Information Security Officers (CISOs) are becoming an integral part of the corporate hierarchy as enterprises begin to take security concerns more seriously. It’s a smart move considering that in 2019 security breaches cost companies on average $3.92 million. Now in 2020, CISOs are facing accelerating old threats along with some brand new ones. Here are the top eight CISO concerns of 2020:
Read More2019 Data Breaches By the Numbers
We looked at trusted sources in our industry like the Ponemon Institute, FBI Internet Crime Complaint Center (C3), and Global Market Insights to round up the top numbers you should know about data breaches that happened over the past year.
Read MoreMixMode Now Supports Amazon VPC Flow logs
We’re excited to announce the general availability of support for Amazon Web Services’ VPC Flow Logs, in the MixMode platform! MixMode prides itself in offering a heterogeneous, “single pane of glass” view and analysis into multiple kinds of workloads, including both On-Premise and Cloud workloads.
Read MoreFeatured MixMode Client Success Story: Nisos
After suffering a possible breach, a client approached the team at Nisos for help evaluating the security of their AWS environment. The client was concerned about possible malicious activity on the part of a former employee who had maintained an AWS Identity and Access Management (IAM) account after being separated.
Read MoreA Well-Equipped Security Team Could Save You Millions of Dollars a Year
Data breaches are expensive. By now, most organizations are well aware of this fact. When it comes to resource planning, however, SecOps teams need concrete data to ensure adequate funding is available to handle a breach.
Read MoreNetwork Data: The Best Source for Actionable Data in Cybersecurity
With the right tool, your network data can now provide you with most valuable, actionable alerts in your security stack. What follows is a discussion of some of the reasons why you may want to look to your network first when trying to identify potential threats or attacks.
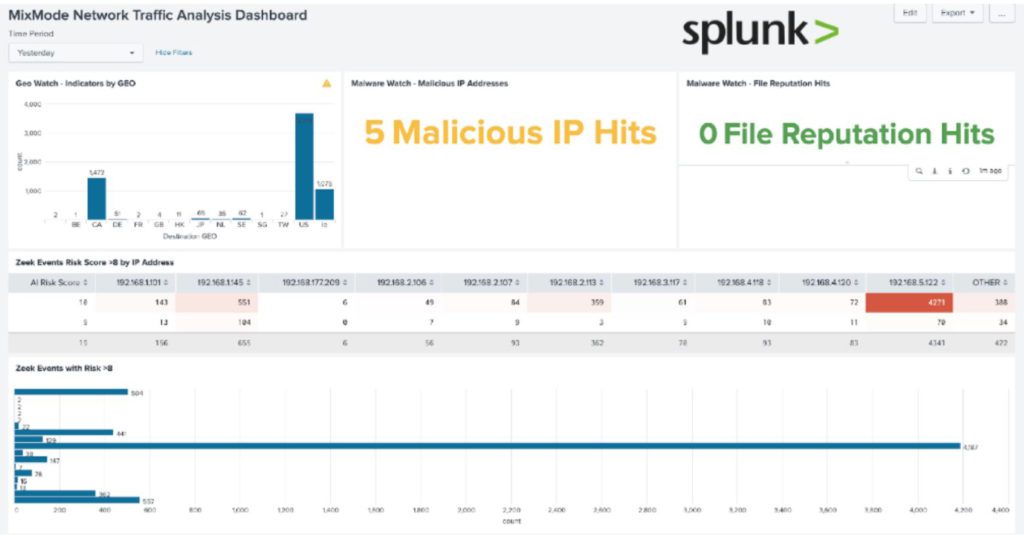
Read MoreUsing the MixMode query language to integrate with splunk
Integrating MixMode with Splunk provides immediate AI based decision making to your organization. This results in fewer alerts, and more actionable data for analysts to consume.
Read More3 Cyberthreats Facing Federal and State Governments in 2020
Bad actors do not discriminate. Organizations across all sectors are at risk — corporations, non-profits, and increasingly, federal and state government entities. The U.S. Government Accountability Office (GAO) reported that security incidents increased by 1,300 percent from 2006 to 2015. This number is growing.
Read MoreStaying CCPA Compliant with MixMode’s Unsupervised AI
Companies are expected to spend up to $55 billion dollars on efforts to comply with the California Consumer Privacy Act (CCPA), which is still working out its final rules after going into effect this month.
Read More