Mixmode Blog
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
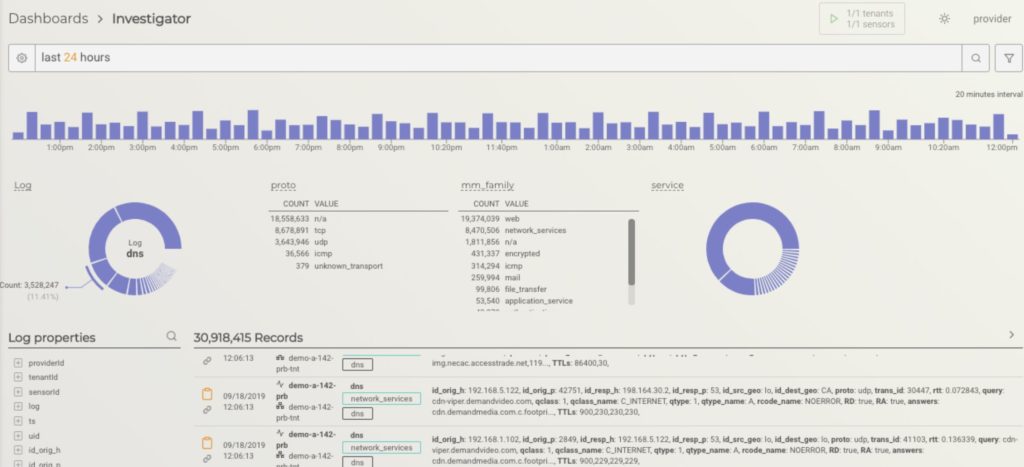
MixMode 6.1.8 Investigator – Massive Data, Optimum Performance
When revisiting Mixmode API eliminating data over-fetching was one of the key areas that we focused on for our 6.1.8 release.
Read More4 Ways to Protect Your Business from Zero-Day Attacks
Zero-day attacks cost businesses millions of dollars in lost revenue and recovery costs and can cripple a company that is not prepared to respond decisively and effectively.
Read MoreWhy Unsupervised Machine Learning is the Future of Cybersecurity
Not all Artificial Intelligence is created equal. As we move towards a future where we lean on cybersecurity much more in our daily lives, it’s important to be aware of the differences in the types of AI being used for network security.
Read MoreThe Difference Between Artificial Intelligence and Machine Learning in Network Security
Artificial Intelligence (AI) and Machine Learning (ML) are often used interchangeably when discussing developments in deep learning. However, there is an important difference between the two that network security professionals will need to understand in order to serve their clientele effectively.
Read MoreUnsupervised AI as a Service: Predictive Intelligence for Cybersecurity
The cybersecurity industry is in need of a massive shakeup. Rules-based software has created an exponential increase in false positive security alerts and zero-day threats are on the rise.
Read MoreAnomaly Detection with Unsupervised AI in MixMode: Why Threat Intel Alone is Not Enough
In the face of intelligent cyber threats, the best defense is to supplement traditional methods with anomaly detection through unsupervised artificial intelligence (AI).
Read MoreImprovements to MixMode’s PQL: Packetsled Query Language
Packetsled Query Language (PQL) addresses the need of analysts to ask questions from large amounts of data without being forced to learn a complicated query language. It is a simple, intuitive expression language that lets users focus on finding what they need quickly.
Read MoreFalse Positives and Negatives: The Plague of Cybersecurity Software
Whether your network analysts are spending too much time on false positives or neglecting to recognize false negatives, when actual cyber threats go unnoticed, fear not. Here are 4 ways to combat false positives and negatives in your network security program.
Read MoreA third of experts predict cybersecurity won’t need human decision-makers within a decade: This Week in AI
Recent cybersecurity news, trends, and highlights and how artificial intelligence (AI) is transforming the industry.
Read More