4 Ways to Protect Your Business from Zero-Day Attacks
When zero-day attacks happen, the way you respond can impact your entire organization and damage the trust you have built with your client base.
These attacks cost businesses millions of dollars in lost revenue and recovery costs and can cripple a company that is not prepared to respond decisively and effectively. These attacks have become increasingly common over the past few years. According to the Ponemon Institute’s 2018 State of Endpoint Security Risk Report, 76 percent of successful attacks on organization endpoints in 2018 were zero-day attacks.
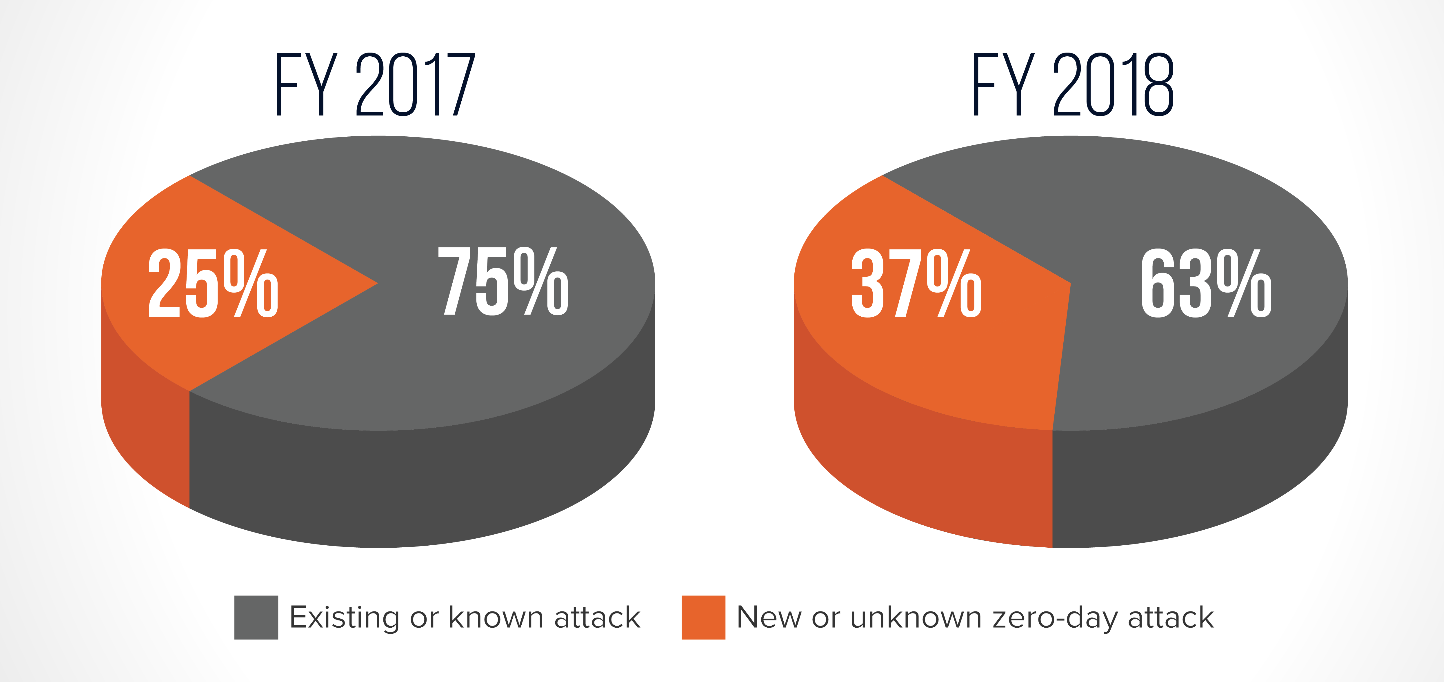
*Zero-Day attacks grew 12% between 2017-2018
Many companies stop short of fully acknowledging the potential damage that can be caused by zero-day attacks, choosing to rely on traditional antivirus solutions. However, the above-referenced Ponemon Institute research revealed that IT professionals believe these measures can only stop around 43 percent of attacks.
Malware serves as a particularly attractive inroad for zero-day exploitation. 30 percent of malware attacks can be classed as zero-day attacks, almost always through email (93 percent of the time).
Exploring recent zero-day attacks on prominent companies and organizations can reveal commonalities in method and execution. We can also gain some hindsight perspective into how these entities might have been able to prevent or limit the attacks.
Case Studies: Recent Zero-Day Attacks
The DNC Hack
The 2016 Democratic National Committee (DNC) breach was the result of a zero-day attack. Russian hackers were able to exploit six zero-day vulnerabilities to gain access to private data. Microsoft Windows and Devices Group executive vice president Terry Myerson pointed to two zero-day vulnerabilities in Java, Adobe Flash and the down-level Windows 10 kernel that allowed the hackers to target a specific set of customers (the DNC) through spear-phishing tactics.
Zoom Webcam Hijack Attack
The Zoom zero-day attack shows us that Mac customers are not immune from being targeted by malicious hackers. Here, a Zoom user’s web camera was hijacked when hackers targeted a vulnerability in the popular web-conferencing software that switched on participants’ web cameras when they accepted a meeting request. Worse, any Mac user who has used Zoom at any time is still at risk thanks to the localhost web server Zoom leaves on the machine. A victim need only visit a webpage for Zoom to independently reinstall itself. The attack has no doubt created a serious headache and trust issue for Zoom.
Windows Four Horseman Zero-Day Attack
This recently uncovered attack is especially severe. The attacker can install programs; view, change, or delete data; or even create entirely new accounts that grant them full user rights. This flaw (CVE-2019-0859), targeting 64-bit versions of Windows, is a use-after-free issue in the Windows kernel that allows local privilege escalation. This attack is an example of the limitations of traditional antivirus approaches – the attacker has used Window’s built-in PowerShell program to help hide their activities from being detected by antivirus software.
4 Ways You Can Limit Zero-Day Risk
While it would be impossible to mitigate every foreseeable zero-day risk, there are several actionable steps any company, small or large, can take to lower that risk.
1. Keep your software up-to-date.
2. Check for a solution when a zero-day vulnerability is announced and apply the patches that software vendors release.
3. Don’t underestimate the threat. Cybercriminals work continually to uncover and exploit security holes, including those that can grant them full access to your devices. The personal, identifying information they can access about you, your employees and your customers can open victims up to identify theft, bank fraud, and even ransomware.
4. Use AI to predict and identify zero-day attacks in real time. Mixmode’s third wave AI tools create a baseline understanding of a company’s network and identify anomalies as they occur, allowing zero-day attacks to be alerted on as they happen in real time.
A Final Note
If your SecOps team is not prepared to respond to or prevent a zero-day attack, be sure to arm them with information about this increasingly common hacking method. Many of your zero-day vulnerabilities can be eliminated when you equip your network with the real-time AI solutions Mixmode can provide.
Schedule a Mixmode demo today so that you can identify, investigate, and respond to threats in real time with AI-enabled network security.
MixMode Articles You Might Like:
Why Unsupervised Machine Learning is the Future of Cybersecurity
The Difference Between Artificial Intelligence and Machine Learning in Network Security
Unsupervised AI as a Service: Predictive Intelligence for Cybersecurity
How MixMode’s AI Builds Your Network’s Baseline
Turning the Unsupervised Tables on the Turing Test
Top 5 Ways AI is Making Cybersecurity Technology Better
What is Network Detection and Response (NDR)? A Beginner’s Guide


