MixMode Platform Update: Support for Google Cloud
MixMode is proud to release our platform sensor for Google Cloud!
With this capability, customers can now monitor their Google Cloud infrastructure for security anomalies and zero-day attacks, using the same industry-recognized MixMode platform enterprises already use for on-premise security monitoring, Amazon Web Services monitoring, and Microsoft Azure monitoring.
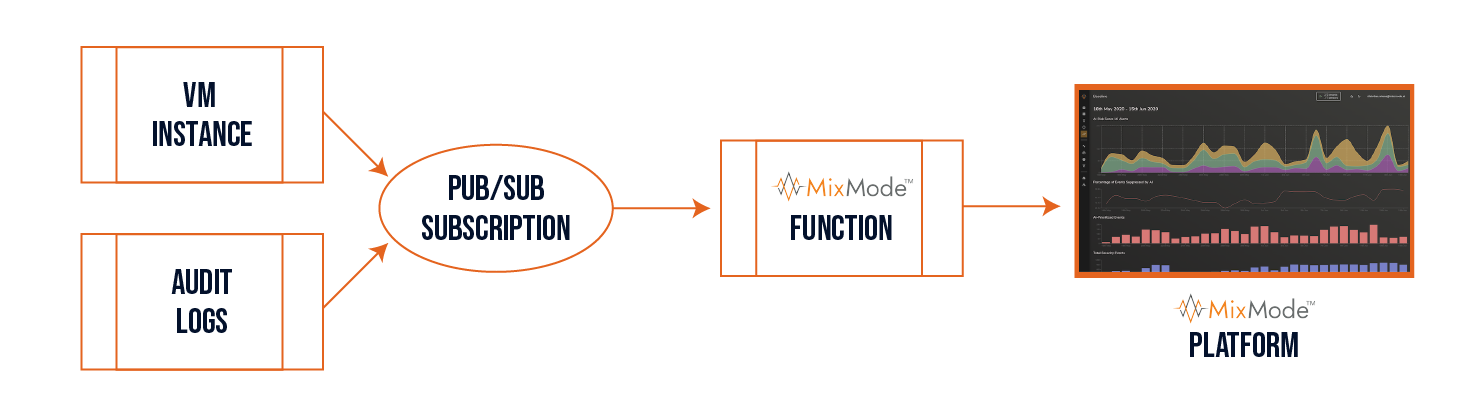
MixMode’s Google Cloud sensor can tap into two different aspects of Google Cloud activity: Flow Logs, which track data in and out of your virtual machine fleet, and Activity Logs, which track usage of Google APIs by your applications. These two surface areas complement one another and together offer nearly complete coverage across the Google Cloud environments.
With this new integration, operators can do the following:
- Read from a Google “Pub/Sub” subscription pipeline stream of log entries,
- Process Flow and Audit (Activity) Log entry data to be formatted for MixMode ingestion, and
- Securely transmit the reformatted data to a MixMode platform for monitoring and threat detection.
According to GCP documentation “VPC Flow Logs record a sample of network flows sent from and received by VM instances, including instances used as Google Kubernetes Engine nodes. These logs can be used for network monitoring, forensics, real-time security analysis, and expense optimization. Flow logs are aggregated by connection from Compute Engine VMs and exported in real time. By subscribing to Pub/Sub, you can analyze flow logs using real-time streaming APIs.”
When VPC Flow Logs are enabled and configured to send to a “Pub/Sub” subscription, the MixMode Function will process and forward those flow logs to the MixMode Platform.
Cloud Audit Logs maintains three audit logs for each Google Cloud project, folder, and organization: Admin Activity, Data Access, and System Event. Google Cloud services write audit log entries to these logs to help you answer the questions of “who did what, where, and when?” within your Google Cloud resources.
The same MixMode Function is capable of processing Cloud Audit Logs when the Audit (Activity) Logs are configured to write to the same “Pub/Sub” subscription.
MixMode will provide instructions to:
- Create and configure the Google Cloud Function with supplied data
- Create a Google ‘Pub/Sub’ subscription pipeline to read
- Configure both VPC Flow Logs and Cloud Audit Logs to sink to the newly created Google ‘Pub/Sub’ pipeline


