Securing Your Cloud Environment: Understanding and Addressing the Challenges in Cloud Security
According to a recent study by Gartner, 85% of enterprises will have embraced a cloud-first strategy by 2025. This trend is driven by the increasing demand for cloud-based applications and services and the growing maturity of cloud platforms.
Unsurprisingly, enterprises are increasingly migrating to the cloud, given the promise of better performance, scale, accessibility, and economics.
Benefits of Migrating to a Cloud Environment
Some of the key benefits of cloud migration for enterprise organizations include the following:
- Scalability: Cloud computing offers unlimited scalability, so businesses can quickly scale their operations up or down as needed. This can help to improve efficiency and reduce costs.
- Flexibility: Cloud computing is highly flexible, so businesses can choose the services they need and pay only for their use. This can help to save money and improve agility.
- Cost savings: Cloud computing can help businesses to save money on IT infrastructure costs. Companies do not need to purchase and maintain their hardware and software.
- Accessibility: Data and applications can be accessed easily from any inter-connected device, enabling collaboration and a remote workforce.
- Compliance: Cloud providers can help businesses to comply with government regulations. This can help businesses to avoid costly fines and penalties.

However, cloud migration has its risks.
As enterprises rapidly migrate critical infrastructure and data to the cloud, they lose visibility and control. A recent report shows 80% of organizations encountered a significant security incident related to their cloud infrastructure within the past year.
Risks associated with migrating to a cloud environment
It’s imperative to understand the related risks of migrating to a cloud environment, including the technology blind spot that organizations may face during the migration process through:
- Overlooking vulnerabilities and security gaps.
- Improper configurations can expose sensitive data and applications to cyber attacks.
- Increased risk of unauthorized access and data breaches is a concern when multiple users access the same cloud services and data.
Additionally, the dynamic nature of cloud environments poses a continuous change risk. As cloud services and technologies rapidly evolve, organizations must keep up with updates, patches, and new security threats. Failure to do so can result in outdated security measures, leaving the organization vulnerable to attacks.

Measuring Risk Exposure in the Cloud
Measuring risk exposure in the cloud environment is crucial for organizations to ensure the security of their data and infrastructure. Organizations need to consider several factors to gain insight into their level of risk and take appropriate measures to mitigate it. This includes:
- The number of users accessing the cloud infrastructure: The higher the number of users, the greater the potential for security breaches. Organizations should closely monitor user access privileges and implement robust authentication mechanisms.
- Securely configuring the cloud infrastructure: Organizations should ensure all security controls are correctly implemented and maintained. This includes regularly updating and patching systems, securely storing and managing encryption keys and monitoring for misconfigurations.
- Security teams’ level of familiarity and training in handling cloud incidents: Organizations should have a well-trained and proactive incident response team to detect and respond to security incidents promptly.
- Regular testing and exercising processes: Organizations can proactively identify and address potential weaknesses by conducting regular penetration testing and vulnerability assessments before they can be exploited.
Blind Spots Created by Cloud Security
Cloud security blindspots are created by the unique characteristics of cloud environments, which differ from legacy data centers that security tools were initially designed for. Public cloud platforms have transient infrastructure, geographic distribution, and shared responsibility models that disrupt traditional security approaches.
One of the leading blind spots is limited visibility across the cloud environment. While the cloud provider is responsible for securing the underlying infrastructure, the client is responsible for securing their applications, data, and user access. This division of responsibilities can lead to gaps in security monitoring and incident detection, as the client may need complete visibility into the cloud provider’s security measures and logs.
According to Gartner, many cloud security failures can be attributed to customer misconfigurations and mistakes. This highlights the challenges and responsibility of an enterprise in ensuring a secure cloud environment. Misconfigurations such as weak access controls, improper encryption, or inadequate monitoring can create vulnerabilities that bad actors can exploit.
A holistic approach is needed to eliminate cloud security blind spots. This includes continuously inventorying all assets, applying policies and controls at scale, integrating with cloud access logs and events, and focusing on workloads and data flows rather than just infrastructure. Leveraging cloud-native capabilities for security is also key, rather than using inadequate legacy toolsets.

Challenges of Security In Cloud Environments
Cloud environments are complex and dynamic, which makes them difficult to secure. Here are some of the challenges:
- Scale and complexity: Cloud environments can have hundreds of thousands of assets, making tracking and securing them all problematic.
- Shared responsibility model: Cloud providers and customers share responsibility for security, which can lead to confusion and gaps in coverage.
- Proprietary applications and services: Proprietary applications and services may not integrate well with security tools, creating blind spots.
- Dynamic, borderless, and unstructured environments: Cloud environments constantly change, making it difficult to maintain security controls.
To address these challenges, organizations need to adopt a cloud-first security strategy. This includes:
- Using cloud-native security tools and services.
- Implementing a zero-trust security model.
- Automating security tasks.
- Training employees on cloud security best practices.
These steps can help organizations reduce their risk of potential security breaches in the cloud.
How Cloud Security is Different than Traditional Security Solutions
Cloud security differs from traditional solutions in that the organization and the cloud provider share responsibility for security. In traditional solutions, the organization is solely responsible for security, while the cloud provider is only responsible for the underlying infrastructure.
In the cloud security model, the organization is responsible for securing its applications, data, and user access, while the cloud provider is responsible for securing the underlying infrastructure, such as servers, networks, and physical data centers. This shift is important because it relieves the organization of managing and maintaining security infrastructure, allowing them to focus on their core business processes. It also means that the cloud provider must have robust security measures to protect their infrastructure and prevent unauthorized access or data breaches.
The shared responsibility model of the cloud requires organizations to take adequate measures to secure their environment, applications, and data. Failing to do so can lead to breaches with severe business impact. A proactive approach to identifying and mitigating cloud security risks remains critical.
Download our eBook to learn more about the critical differences between traditional and cloud security and what is needed to support a cloud-first strategy.
How MixMode Can Help
The Mixmode Platform is a cloud-native, real-time threat detection and response solution that helps organizations secure their entire cloud infrastructure, capable of correlating large volumes of diverse cloud data from multiple sources and surfacing relevant threats.
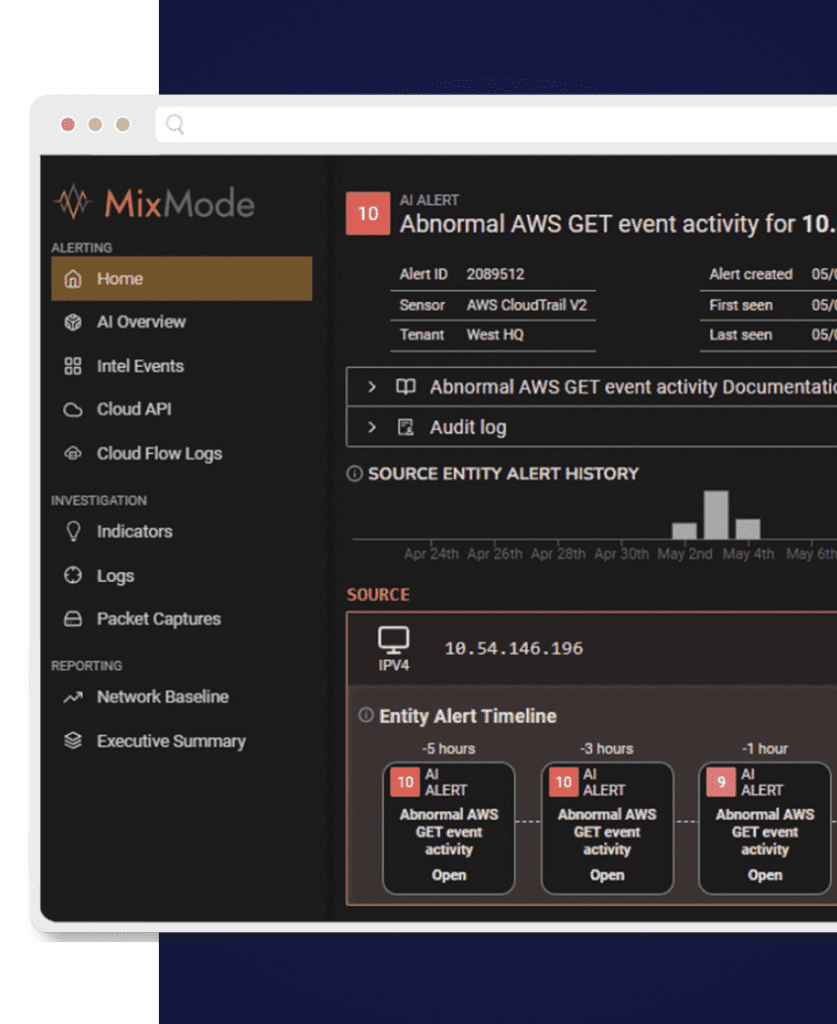
The MixMode Platform is the only generative AI cybersecurity solution built on patented technology purpose-built to detect and respond to threats in real-time, at scale. MixMode’s generative AI is uniquely born out of dynamical systems (a branch of applied mathematics) and self-learns an environment without rules or training data. MixMode’s AI constantly adapts itself to the specific dynamics of an individual network rather than using the rigid legacy ML models typically found in other cybersecurity solutions.
With MixMode, security teams can increase efficiencies, consolidate tool sets, focus on their most critical threats, and improve overall defenses against today’s sophisticated attacks.
MixMode’s cloud-native adaptability makes it easy to install and run across AWS, Azure, GCP, and many other cloud platforms and cloud-based applications in only minutes.
Reach out or download our eBook to learn more.


.png)