The Fallacy of “One-Click Remediation”

The following is an excerpt from our recently published whitepaper, “Is ‘One-Click Remediation’ Intentionally Misleading SOC Teams?,” in which we discuss the misleading “one-click remediation” claims that many cybersecurity tool vendors are using in the marketplace.
The Fallacy of “One-Click Remediation”
Let’s take a closer look at the false narrative being propagated in the cybersecurity market and explore some more appropriate alternatives. An example of a legacy cyber tool vendor “feature” being touted as an ideal solution to the problem of automatic remediation is reliant on a standard (though rarely used for reasons we will explore in this article) function known as TCP Reset.
TCP reset is an abrupt closure of the network session causing the resources allocated to the connection to be immediately released and all other information about the connection to be erased. This function simply terminates a connection between source and destination.
Network Traffic Analytics (NTA) and Security Orchestration and Response (SOAR) vendors in particular, have made false claims that by invoking a TCP Reset, SOC teams can ignore alert triage, and automatically address cyberattacks that have gone undetected by the firewall, endpoint, SOC teams, as well as rule and threshold controls from supporting systems, to isolate the user or asset before damage is done.
While the vendors make claims about using complex machine learning and algorithms to invoke a TCP reset, a quick review of their supporting literature references exclusively rule, threshold, and signature based controls (typically tied to connection volume), that are manually created and maintained by teams of machine learning and SOC operators.
Which begs several important questions:
Seems simple enough, why doesn’t everyone deploy simple, automated, TCP Reset controls?
While invoking a TCP Reset is a relatively simple function, and one that can be invoked and deployed easily by most cybersecurity vendors, it’s not widely used because of the inherent risk to normal business functions.
With no supporting context, and significant risk to the disruption of normal and required business functions, terminating connections based on a higher than typical volume is less than ideal and unreasonably disruptive for most customers.
Simply put, the risk of incorrectly blocking normal and appropriate business functions outweighs the reward. Worse, cyber tools utilizing rule-based TCP reset functions are ideal targets for hackers and foreign nation states launching attacks. The tools themselves are easily identifiable by nefarious actors, and the functions they invoke can be more easily invoked inappropriately, to disrupt normal business operations.
Is the ever expanding creation, maintenance, and duplication of rules and controls really a viable solution? Aren’t these controls typically implemented and maintained elsewhere?
Creation and maintenance of multiple rule, threshold, and control lists continues to be both an ineffective and resource intensive challenge for all Security Operations Centers. While once considered essential for known attack scenarios, according to analysts, >80% of recent successful attacks in the have been “novel” attacks, purposefully designed to circumvent rule and threshold-based systems and controls. Creation and duplication of redundant rules across cyber tools is demonstrably ineffective, costly, and resource intensive.
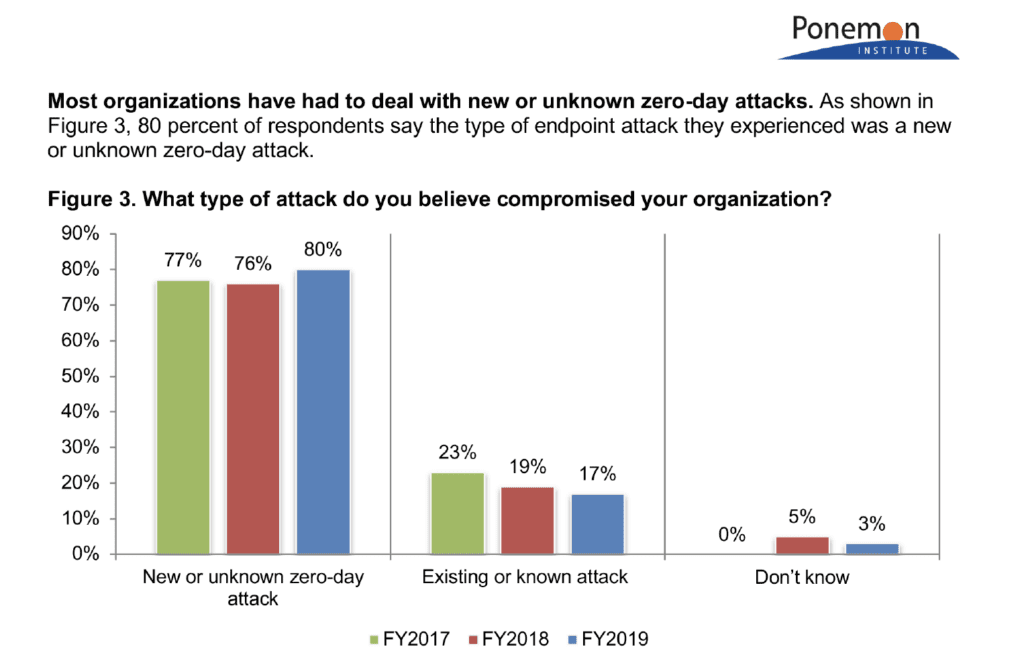
Not surprisingly emphasis on reduction of rule creation in favor of advanced threat and anomaly detection, independent of additive human operators, with supporting context, is now the top priority for most organizations.
Is automatically terminating a connection based on volume of connections really a viable and/or ideal solution?
While potentially viable for the scenarios propagated by the vendors themselves, the examples provided by the vendors are fanciful, self-propagated, and according to most advanced SOC teams, unlikely.
When asked about the scenario outlined by a leading NTA vendor, the CISO for a large US City stated, “If I have a high-volume connection attack that is missed by my next-gen firewall, endpoint, and SOC teams, I have far more significant operational, technical, and security controls issues to address than deploying an NTA originated TCP reset.”
Click here to download and continue reading, “Is ‘One-Click Remediation’ Intentionally Misleading SOC Teams?“
MixMode Articles You Might Like:
Understanding the Evolution and Impact of AI on Cybersecurity
Updated for 2022: What is Network Detection and Response (NDR)? A Beginner’s Guide
Customer Case Study: Self-Learning Cyber Defense for Financial Institutions
False Narratives in the Cybersecurity Tools Market


