The rapid adoption of cloud computing has transformed the way businesses operate. Cloud computing offers organizations several benefits, including scalability, flexibility, and cost savings. However, the rapid shift to the cloud has also created new security challenges.
Organizations are now facing a more complex and dynamic threat landscape. Attackers often target cloud environments because they contain valuable data and applications. Additionally, the distributed nature of cloud environments can make it difficult for organizations to maintain visibility and control over their security posture.
The new State of Cloud Security Report from MixMode summarizes input from 588 security professionals and reveals significant gaps in organizations’ abilities to secure cloud platforms and workloads. Despite multi-cloud adoption reaching mainstream levels, critical capabilities for cloud security, such as real-time threat detection and response, comprehensive visibility, workload protection, and data security, still need to be improved.
This report identifies the top cloud security challenges, assesses the effectiveness of current tools and controls, and outlines what enterprises need to achieve robust cloud security postures.
Concern over cloud security is running high
The report underscores that security concerns related to cloud adoption are widespread. An alarming 75% of respondents indicate they are extremely or very concerned about cloud security, citing risks associated with data breaches, targeted attacks, insecure interfaces, and malicious insiders. This underscores a pressing need for security modernization to match the innovation velocity of cloud environments.
Multi-cloud strategies increase complexity for security teams
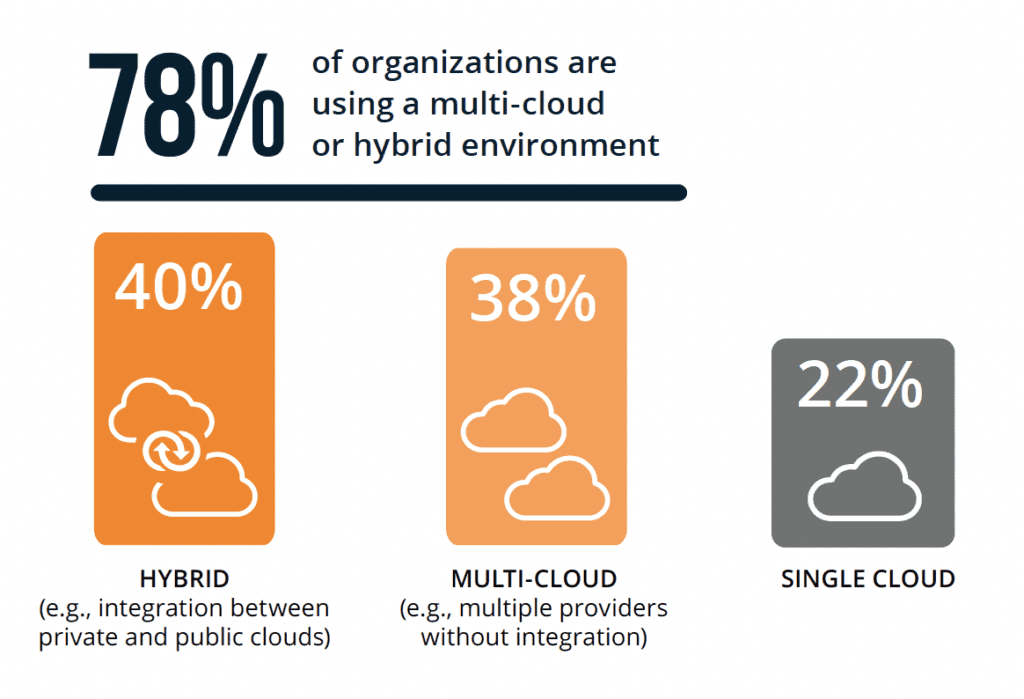
Today, multi-cloud and hybrid cloud deployments are the norm. 38% of respondents report using a multi-cloud strategy spanning AWS, Azure, and GCP, while 40% leverage cloud and on-prem infrastructure. While providing flexibility and redundancy, these heterogeneous environments also increase complexity for security teams. Organizations indicate challenges in getting unified visibility and applying consistent controls across their diverse cloud footprints.
Many still rely on legacy security tools ill-suited for cloud
When assessing specific controls and capabilities applied across cloud environments, the research found extensive reliance on legacy security tools not designed for the cloud. However, these on-prem style tools often lack complete visibility into cloud activity and fail to leverage cloud-native data sources. This signals a gap between organizations’ legacy security stacks and cloud security demands.
Security tool sprawl creates complexity for security teams
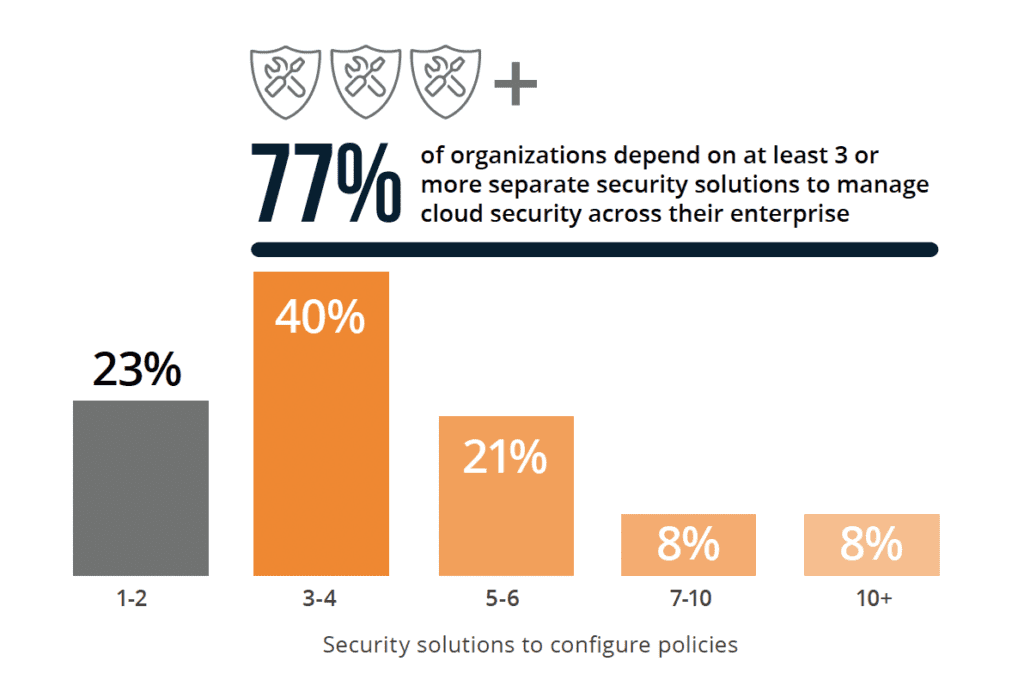
Along with lingering dependence on legacy security products, the research also indicates organizations are deploying multiple-point solutions specifically for cloud security. 77% of organizations depend on at least three or more separate security solutions to manage
cloud security across their enterprise. This underscores a need for consolidation and integration in cloud security strategies, creating tool sprawl and fragmentation.
Real-time threat detection is still lacking for many
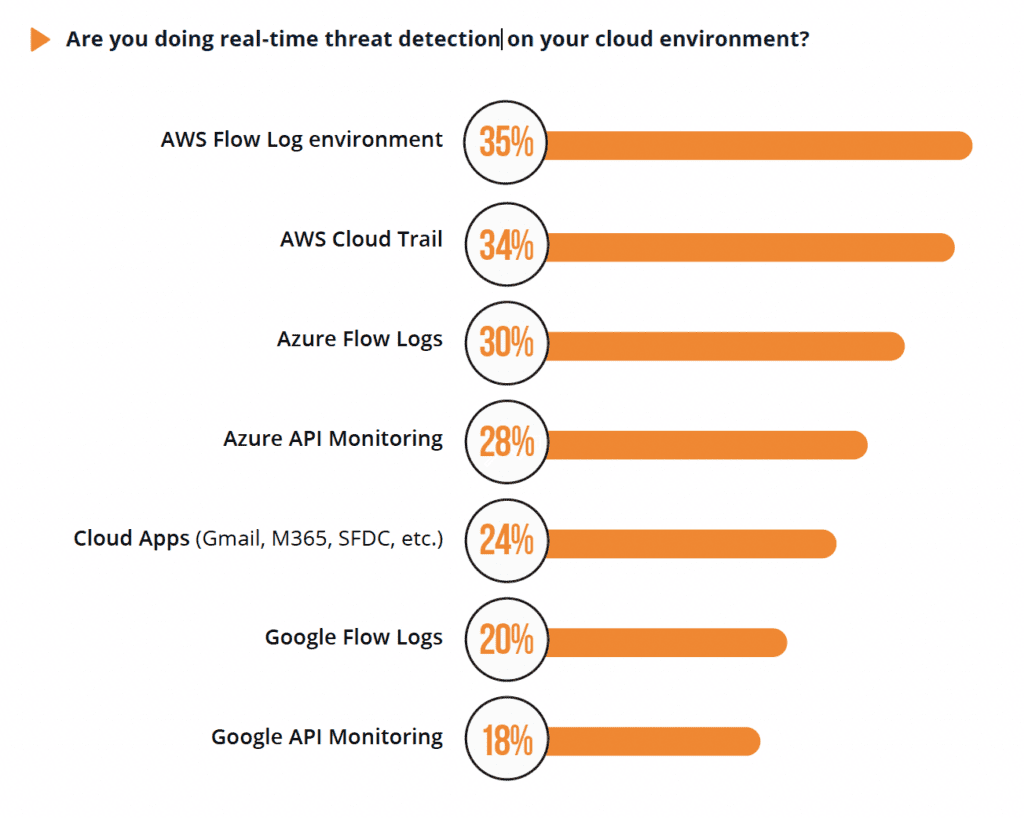
Real-time threat detection across cloud environments is a core capability for effectively securing the cloud. However, the research found significant gaps in this area. Over 65% of respondents are not doing real-time detection in their cloud environment. The report concludes that real-time, behavior-based threat detection is essential for modern cloud environments facing advanced threats.
With security teams already stretched thin, juggling numerous single-purpose tools leads to management headaches, gaps in coverage, and productivity loss. The report shows a growing need for integrated cloud security platforms that connect visibility, threat detection, and response across cloud environments.
The cloud security imperative is clear. Organizations need to take steps to secure their cloud environments from a growing range of threats. This requires a unified, AI-driven security approach providing real-time visibility and protection across all cloud platforms and workloads.
Recommendations
Organizations can improve their cloud security posture by taking the following steps:
- Conduct a regular cloud security risk assessment to identify and prioritize their security risks.
- Implement a unified, AI-driven security solution that can provide real-time visibility and protection across all cloud platforms and workloads.
- Invest in training and education for their security staff to ensure they have the skills and knowledge to secure cloud environments.
- Regularly review and update their cloud security policies and procedures.
The continued adoption of cloud computing has undoubtedly transformed business operations. However, migrating to the cloud introduces new security challenges that traditional tools cannot handle.

How Cloud Threats Differ from Traditional Threats
Threat actors have adapted their techniques to exploit the unique characteristics of cloud environments. Here are some of the key differences:
Dynamic Infrastructure
The infrastructure in cloud platforms is highly elastic. Resources like networks, storage, and computing can be quickly provisioned and released on-demand. Traditional security tools have difficulty keeping up with this rapid rate of change.
Shared Responsibility
In the cloud, the service provider and customer share security responsibilities. Customers must secure their data, applications, identities, and more. Legacy tools don’t have complete visibility into the customer’s realm of control.
Access from Anywhere
Cloud services are accessible from anywhere with an internet connection. This expands the threat landscape to any device trying to reach the cloud. Traditional network perimeters no longer exist.
APIs and Automation
Cloud platforms rely heavily on APIs and automation. API vulnerabilities or misconfigurations can be exploited to gain access or escalate privileges in the cloud.
Architectural Complexity
Cloud architectures involve interconnected services and layers like IaaS, PaaS, serverless, etc. This complex environment allows threats to more easily hide while moving laterally.
Adopting a Cloud Native Security Approach
Because of these differences, securing the cloud requires rethinking your security strategies and tools. Here are some tips:
- Implement security controls closer to your data and workloads in the cloud rather than relying on the legacy data center.
- Choose cloud-based security tools designed specifically for elastic cloud environments versus on-premises tools.
- Take advantage of cloud-native services like serverless security event monitoring and response.
- Use tools with API-level visibility and behavior monitoring to detect API threats.
- Opt for micro-segmentation and zero trust network policies due to the lack of traditional perimeters.
- Continuously monitor for misconfigurations and enforce policies to mitigate configuration risks.
- Leverage automation for scalable, real-time detection and response across your cloud resources.
By adopting a “cloud native” approach, organizations can gain greater visibility, control, and agility in securing critical cloud workloads and data from modern threats.
Enterprises embracing cloud computing and hybrid models must ensure security strategies keep pace. Holistic platforms that harness innovations in AI, behavioral analytics, and cloud architecture can help security teams gain control and strengthen cloud security postures.
How MixMode Can Help
MixMode’s Cloud Detection and Response Solution provides real-time threat detection for your cloud environment, capable of ingesting and analyzing large volumes of diverse cloud data from multiple systems.
MixMode CDR continuously monitors your cloud environment at scale, delivering comprehensive visibility that ensures the defense of your entire cloud infrastructure against known and unknown threats. MixMode’s cloud-native adaptability makes it easy to install and run across AWS, Azure, GCP, and many other cloud platforms in minutes. Click to download the report or reach out to learn more.
Other MixMode Articles You Might Like
MixMode Releases State of Cloud Security 2023 Survey and Cloud Detection and Response for AWS
CISOs: Are You Applying NIST / CISA Standards to ALL Data Including the Cloud?
SEC Adopts New Cybersecurity Risk Management and Reporting Rules: What Businesses Need to Know
Key Takeaways from Black Hat 2023
Cybersecurity Industry Leader Bob Pratt Joins MixMode as Senior Vice President of Product


