We’ve yet to reach the peak of the ransomware crisis impacting organizations around the world, despite an emergent statistic that the attack method now comprises 75% of all global digital espionage campaigns.
New research from Verizon reveals that ransomware is responsible for a sizable percentage of all recorded security incidents. Despite the alarming statistics raised in the report, the tech giant warns, we’re likely to see continued growth in the number of ransomware attacks against organizations.
The annual Verizon Data Breach Investigations Report, released in June, is based on data gleaned from 16,000 security incidents that occurred between November, 2021 and October, 2022. The figure includes 5,000 data breaches. In addition to new information related to ransomware trends, the report outlines several key findings:
- The “log4j” vulnerability was used in 75% of digital espionage campaigns
- Social engineering attacks have doubled, and mostly involve Business Email Compromise (BEC) attacks
- 74% of beaches include the human element, including errors and privilege misuse
- 83% of breaches included external actors
- 95% of attacks had a financial motive
- The three primary methods of access were stolen credentials, phishing, and vulnerability exploitation
Ransomware trends
Around the beginning of 2023, some industry analysts were pointing to a promising trend — ransomware seemed to have dropped in 2022, but it’s clear at the mid-year point that the reprieve was only temporary. Ransomware has jumped back up and remains steady across the past 24 months at around 24% of all cyber attacks.
Verizon reports that outside attacks are mostly attributable to ransomware encryption and extortion tactics. Ransomware is the second most frequently reported attack technique after DDoS, but it is the most frequent technique used by hackers who breach systems.
Verizon is quite clear in the data breach incident report that organizations must take heed to the alarming statistics related to ransomware. While the company writes that it had been anticipating ransomware would soon hit a “theoretical ceiling,” meaning that all incidents that could have ransomware would have, in fact, “Ransomware is present today in more than 62% of all incidents committed by organized crime actors and in 59% of all incidents with a Financial motivation, so sadly there is still some room for growth.”
The report cites the three most common entry points taken by ransomware actors:
- Desktop applications
- Web applications
Notably, only 5% of breaches analyzed in the report included security vulnerability exploitation across systems or devices.
Log4j trend
When the Log4j vulnerability first emerged, the news was ominous. Not only was the bug showing up in numerous widely used commercial systems and software products, but it became quickly apparent that organized cybercrime groups and adversarial nation-states were scrambling to take advantage. Soon, a coordinated effort between private sector organizations and government entities like CISA was underway to eradicate Log4j and contain the spread.
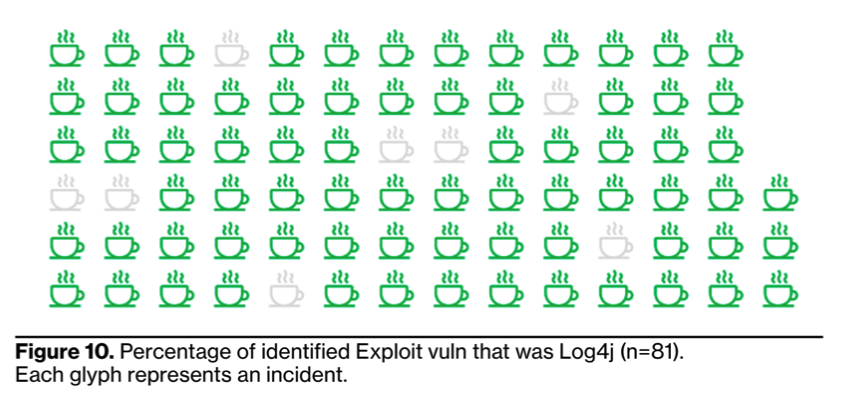
In its report, Verizon speculates that the coordinated effort helped to reduce what could have been a much more severe impact from the bug. Instead, organizations and government entities were able to apply patches quickly, dramatically reducing the number of potential exploits. Still, 73% of breach cases that involved digital espionage and nearly 30% of cases that involved organized crime included the use of the Log4j bug during the analyzed period.
Many breaches originate inside organizations
One of the most revealing (and actionable) outcomes of the data breach incident report is this statistic: Around 20% of breaches tracked by Verizon in the reported period included insider participation. This figure includes both malicious insider attacks and human errors.
“People may think they are somehow immune to a data breach,” the report reads. “They may put their trust in their security controls, thinking they have amazing, impenetrable defenses… But this kind of thinking assumes breaches come from the outside, from the ‘bad actors’ that are external to the organization. What they fail to take into account is the risk of an insider breach.”
The most common non-accidental internal actor breach is privilege abuse, which happens when employees abuse the access they’ve been given to their jobs — mostly, these employees are financially motivated, just like most of the outside bad actors breaking into networks and exploiting bugs.
Putting Verizon’s data breach incident report data to good use
Verizon’s annual report has uncovered many expected and not-so-expected findings that organizations can put to good use when it comes to shoring up their own systems and policies. Proactive investment into modern cybersecurity approaches that incorporate advanced techniques like self-supervised learning and Third Wave AI will significantly increase the likelihood of avoiding attacks designed to bypass legacy cybersecurity systems.
While no tool available today can fully prevent ransomware, MixMode’s highly advanced artificial intelligence, implemented alongside robust processes and good network hygiene can give organizations unprecedented access to preemptive attack identification. MixMode’s AI requires no rules, signatures, or intel feeds and can detect zero-day attacks (think Log4J exploit as one example of many) by understanding an organization’s environment, forecasting expected behavior, and pinpointing anomalous activity related to attacks using code or software vulnerabilities in real-time.
When it comes to detecting insider threats, MixMode’s Third Wave AI generates predictive models of behavior that quickly zero in on threats vs. noise, and identifies anomalous insider behavior that a rules-based system can’t catch.
Find out how MixMode can help your organization gain confidence about mitigating future risks, including ransomware attacks. Reach out to our team to set up a demo today.
Other MixMode Articles You Might Like
Detecting Threats in AWS with MixMode AI
Utilizing Generative AI Effectively in Cybersecurity
AI Offers Potential to Enhance The U.S. Department of Homeland Security


