Critical Microsoft Zero-Day Vulnerability Exploited in the Wild for Over a Year
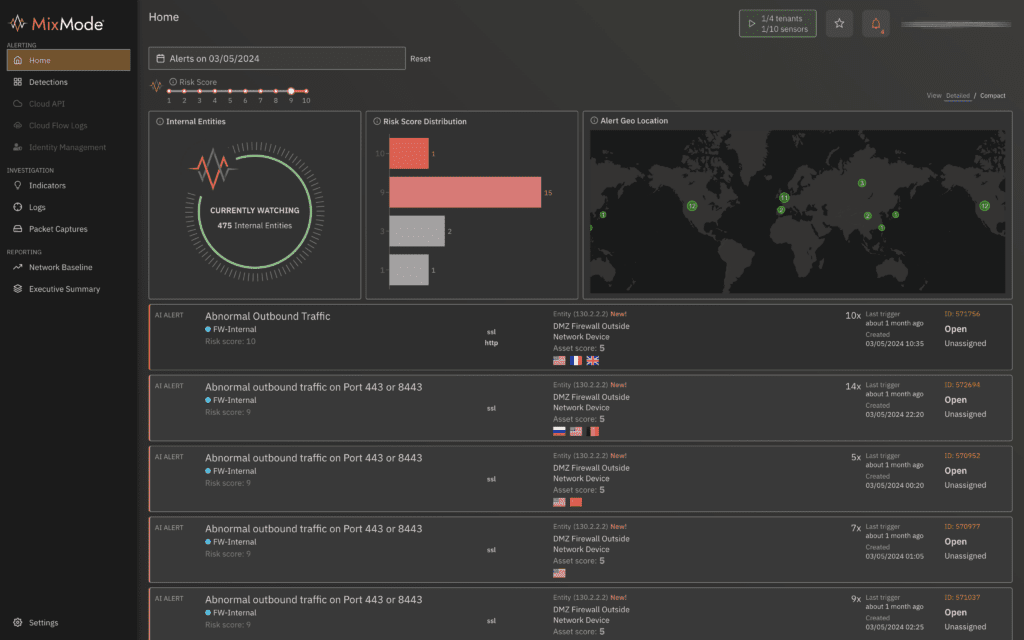
A severe zero-day vulnerability in Microsoft Windows, tracked as CVE-2024-38112, has been actively exploited by threat actors for at least 18 months. This security flaw in the Windows MSHTML Platform allows remote code execution, potentially compromising numerous organizations worldwide.
Critical Microsoft Zero-Day Vulnerability Exploited in the Wild for Over a Year Read More →