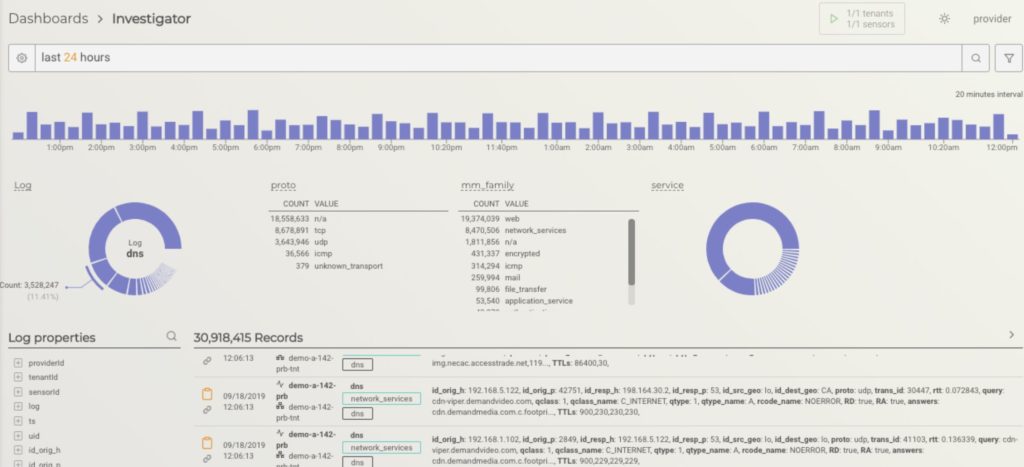
New Video: How is MixMode Different From Today’s Network Security Tools?
With MixMode in the center of a program, we will make all the other security investments that you’ve made, better. So when you send data to your SIEM, when you send data to your SOAR, you don’t want those products to be overwhelmed with false positive alerts, with data you don’t need.
New Video: How is MixMode Different From Today’s Network Security Tools? Read More →